|
|
本帖最后由 gclome 于 2022-1-25 22:56 编辑
原文链接:WeChall CTF平台15题wp(二)
以下题目标题组成:[Score] [Title] [Author]eg. 1 Training: Get Sourced by Gizmore
- Score:1(题目等级)
- Title:Training: Get Sourced
- Author:Gizmore
本篇题目- 0x01 2 Training: LSB by Gizmore
- 0x02 2 Training: GPG by Gizmore
- 0x03 2 Limited Access by wannabe7331
- 0x04 2 Limited Access Too by wannabe7331 and lordOric
- 0x05 2 Shadowlamb - I by Gizmore
- 0x07 2 Repeating History by space and Gizmore
- 0x08 2 PHP My Admin by Gizmore
- 0x09 2 Training: Caterpillar by Gizmore
- 0x10 2 AUTH me by Gizmore
- 0x11 3 Connect the Dots by galen
- 0x12 3 hi by Gizmore
- 0x13 3 Stegano Woman by Z
- 0x14 3 Enlightment by anto
- 0x15 3 Simply Red by anto
0x01 2 Training: LSB by Gizmore
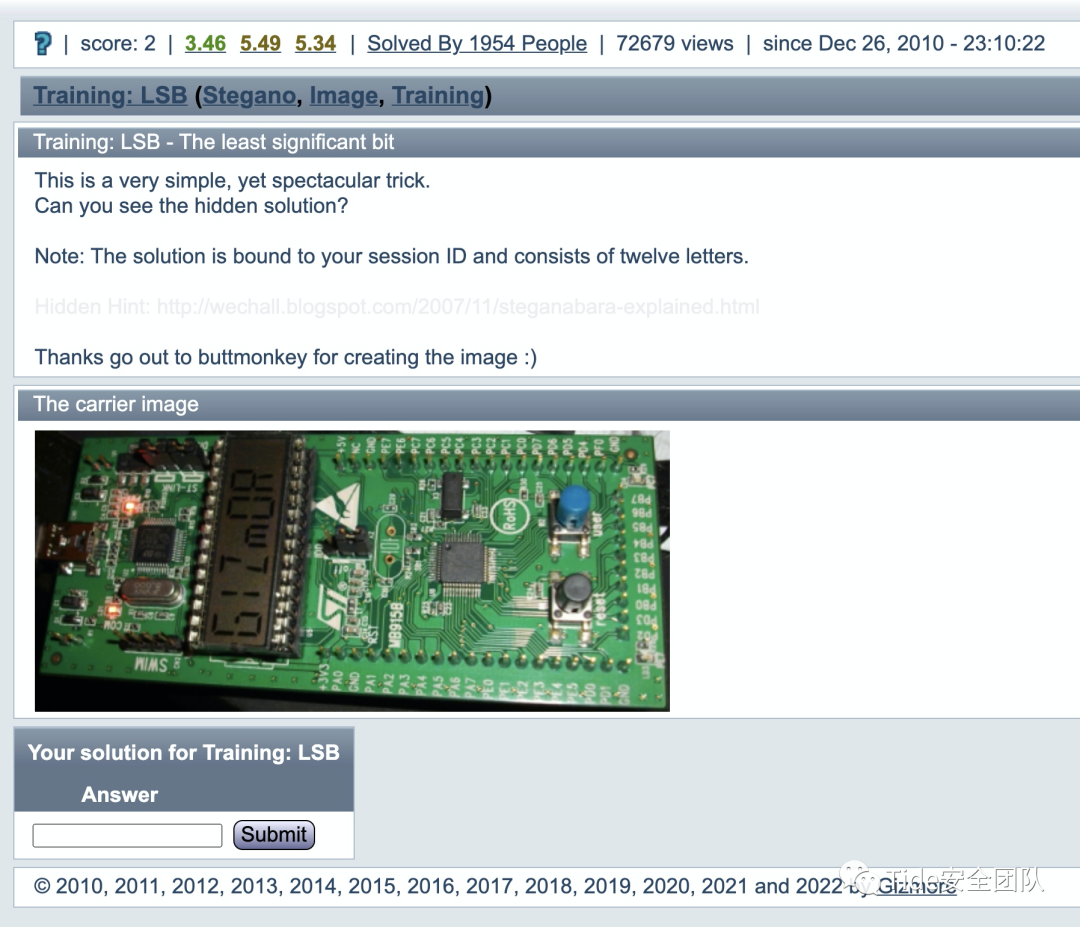 
题目意思:
这是一个非常简单但非常壮观的技巧。
你能看到隐藏的解决方案吗?
注意:解决方案与您的会话 ID 绑定,由十二个字母组成。
隐藏提示:http://wechall.blogspot.com/2007/11/steganabara-explained.html
点开链接提示了工具
不过有一个更好用的被大家公认的工具 -- StegSolve
 
找到答案
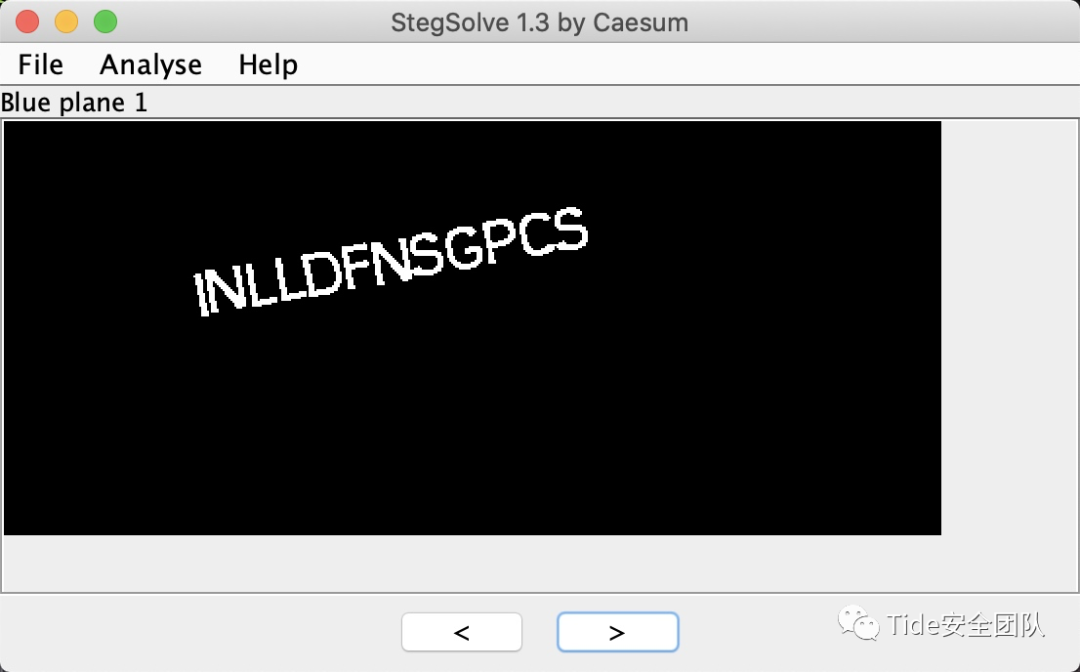 
其次,LSB全称leastsignificant bit,是一种基于图片最低有效位修改储存信息的隐写方法,即使不提供链接,也可以通过题目名称得到tips!
答案:
INLLDFNSGPCS
0x02 2 Training: GPG by Gizmore 
题目意思:
在这个挑战中,您的目标是为您的电子邮件设置 gpg 加密。
为此,请在本地生成您的密钥对并将您的公钥存储在Wechall上。
然后您所有通过Wechall发送的邮件都会被加密。
要启用 GPG 加密,请转到您的帐户设置。
完成后,单击下面的按钮向您发送邮件。
首先了解一下什么是GPG加密
 
安装GPG软件,安装地址
https://gpgtools.org/
 
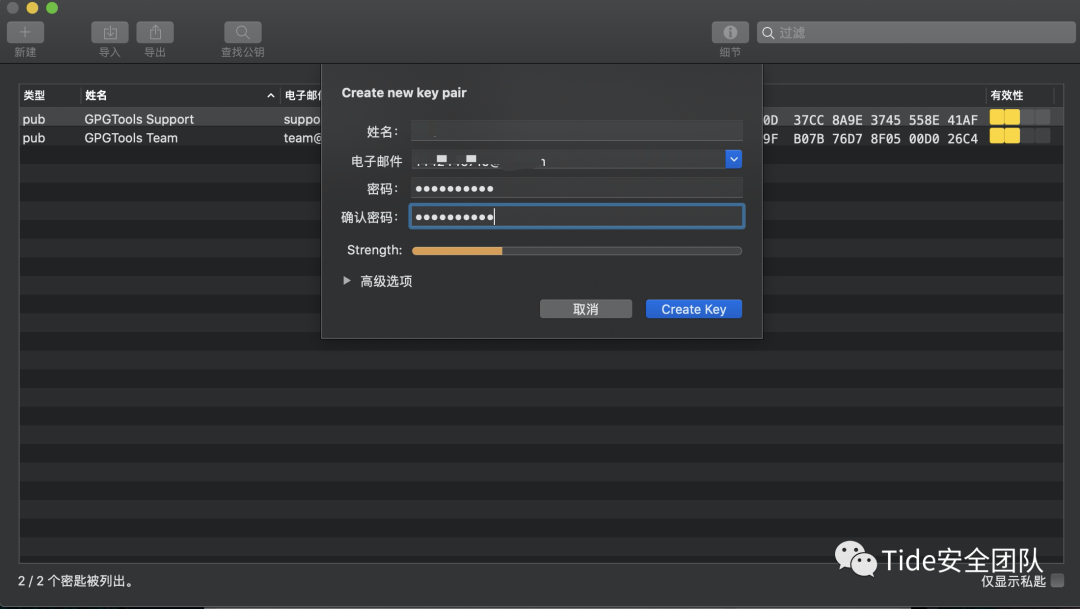 
等待生成密钥
 
导出
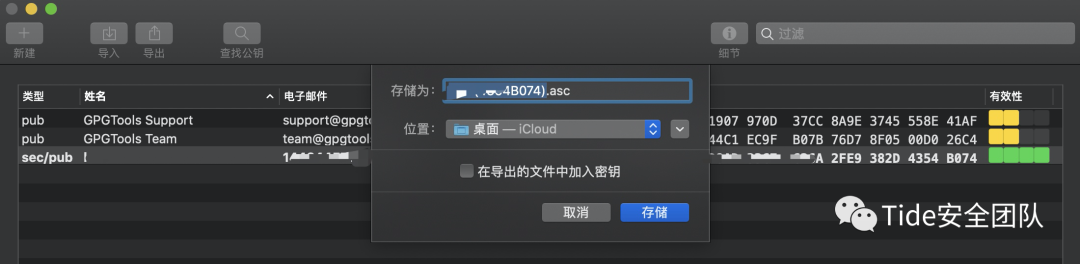 
访问您的帐户设置
https://www.wechall.net/account
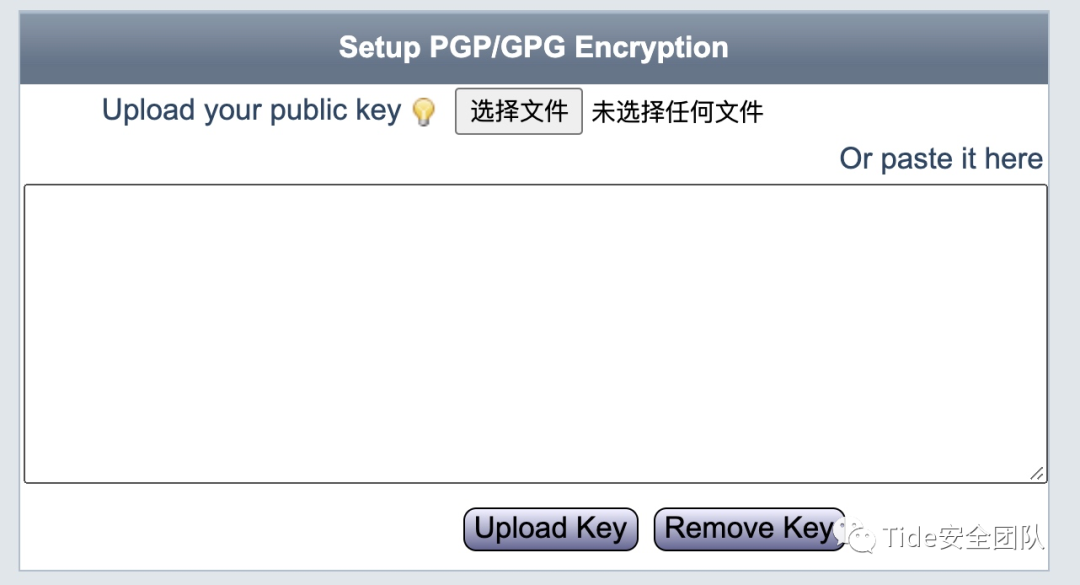
在页面下面会看到这么一个框框,选择文件,上传导出的.asc文件
收到发来的邮件
对比我们导出的邮件????
更改一下我们收到的文件的格式,重命名为.asc文件,之后导入,输入我们新建时候的密码
解密成功
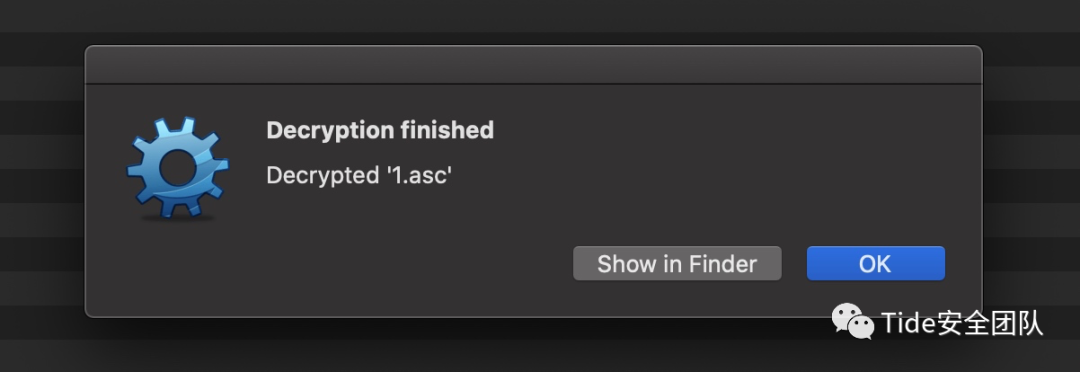 
打开文件
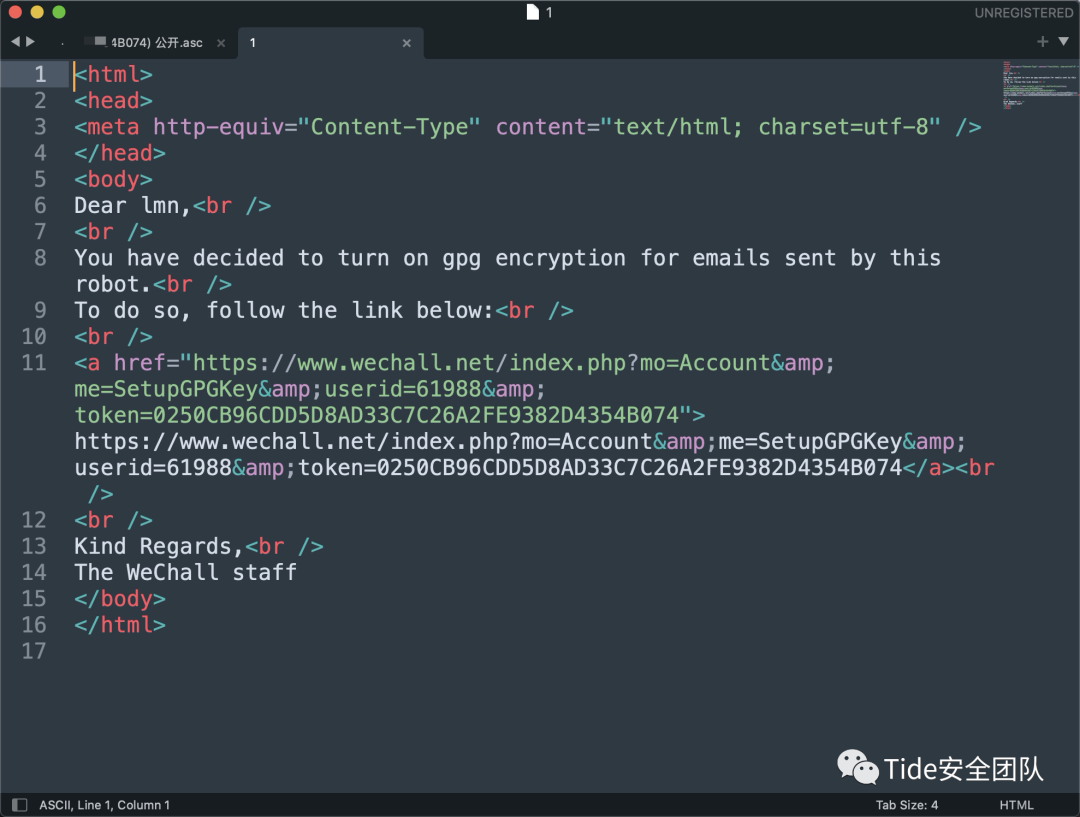 
访问链结后应该后会启动wechall的GPG加密功能,但不是直接copy链接!
后果就是这个
修改后缀为.html,访问链接,bling bling~
进行二次解密
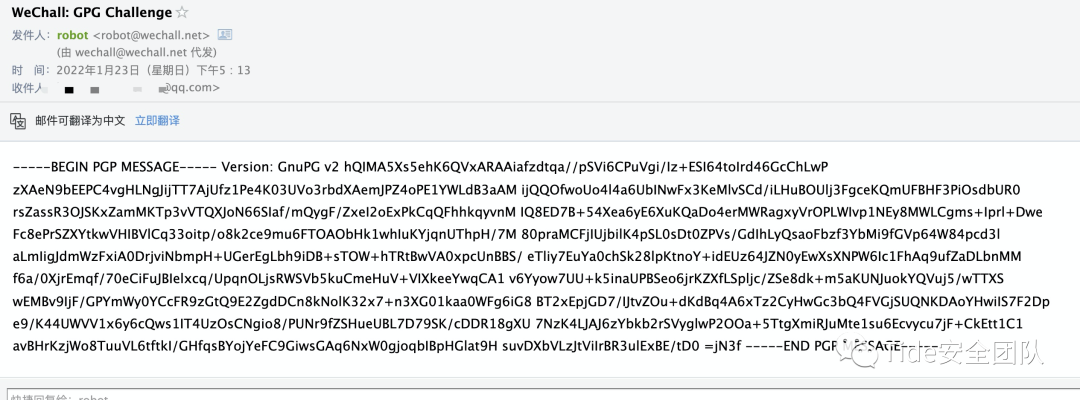 
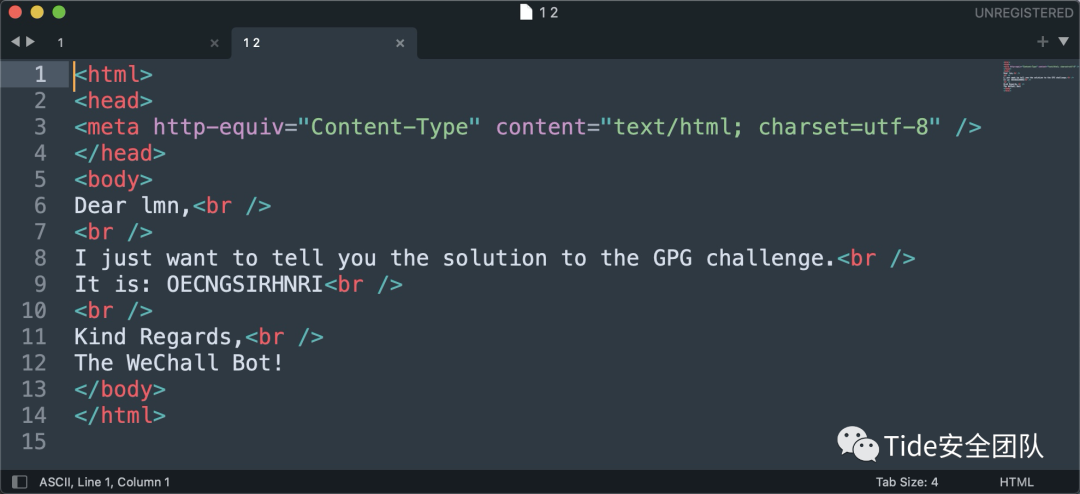 
虽然步骤繁多但是分值是2,不是太难,前提是要了解GPG,得到答案
I just want to tell you the solution to the GPG challenge.<br />
It is: OECNGSIRHNRI
0x03 2 Limited Access by wannabe7331 
题目意思:
我尝试使用.htaccess保护我的页面。我做对了吗?为了证明我错了,请访问 protected/protected.php。
GeSHi`ed Plaintext code for .htaccessAuthUserFile .htpasswdAuthGroupFile /dev/nullAuthName "Authorization Required for the Limited Access Challenge"AuthType Basic<Limit GET>require valid-user</Limit>首先分析这段代码
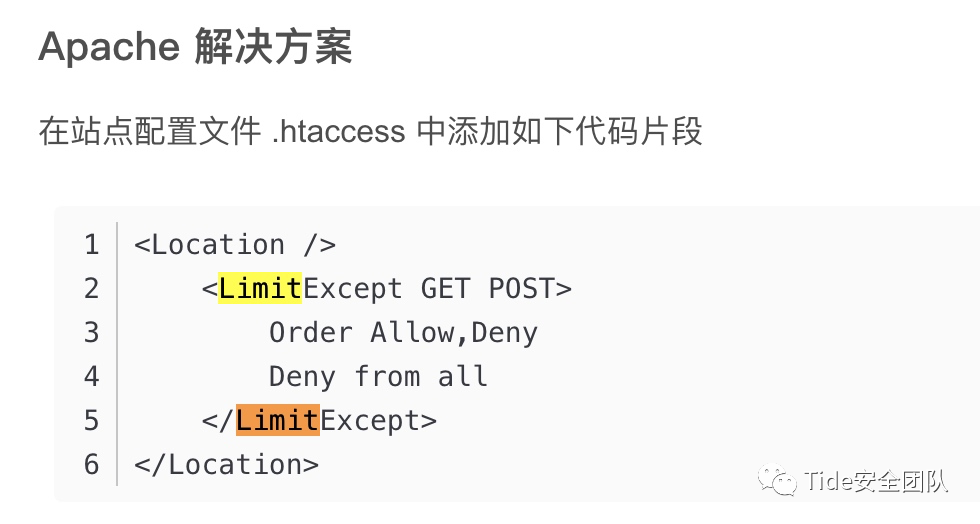 
为只允许GET/POST请求
为不允许允许GET请求
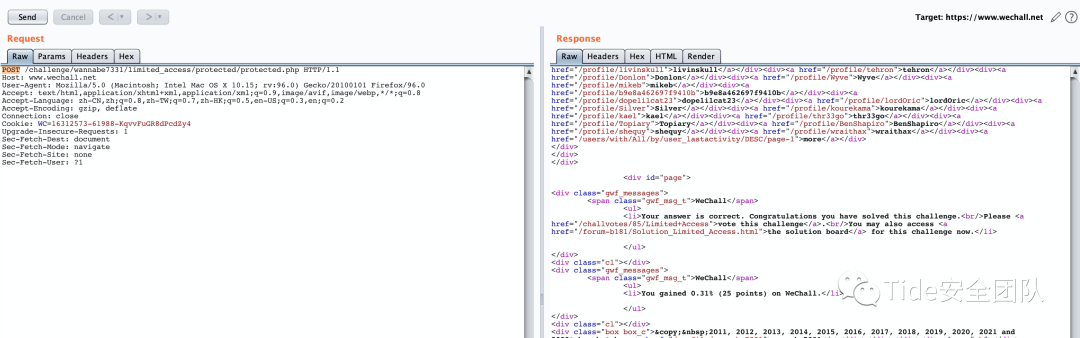 
访问my pages页面,burp抓包修改get为post
 
0x04 2 Limited Access Too by wannabe7331 and lordOric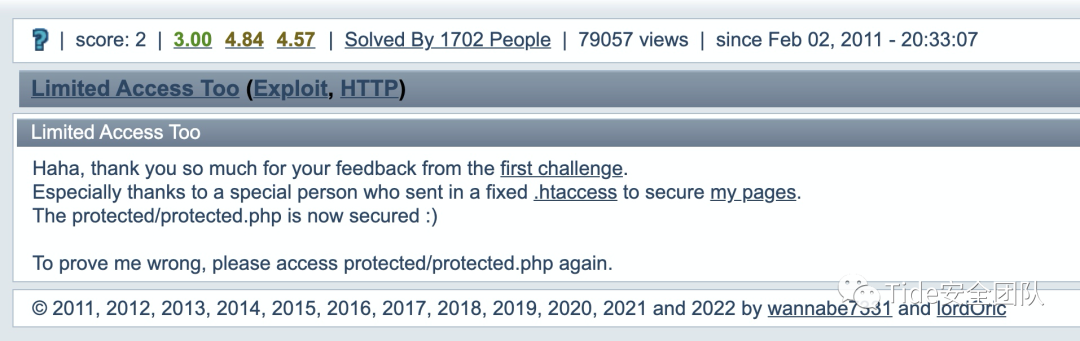 
<Limit GET POST HEAD PUT DELETE CONNECT OPTIONS PATCH>require valid-user</Limit>限制了GET POST HEAD PUT DELETE CONNECT OPTIONS PATCH方法
http的方法有:GET, HEAD, POST, PUT, DELETE, CONNECT, OPTIONS, PATCH, PROPFIND, PROPPATCH, LOCK, UNLOCK, TRACE
urllib.request.Request(url,data = None,headers = {},origin_req_host = None,unverifiable = False,method = None)
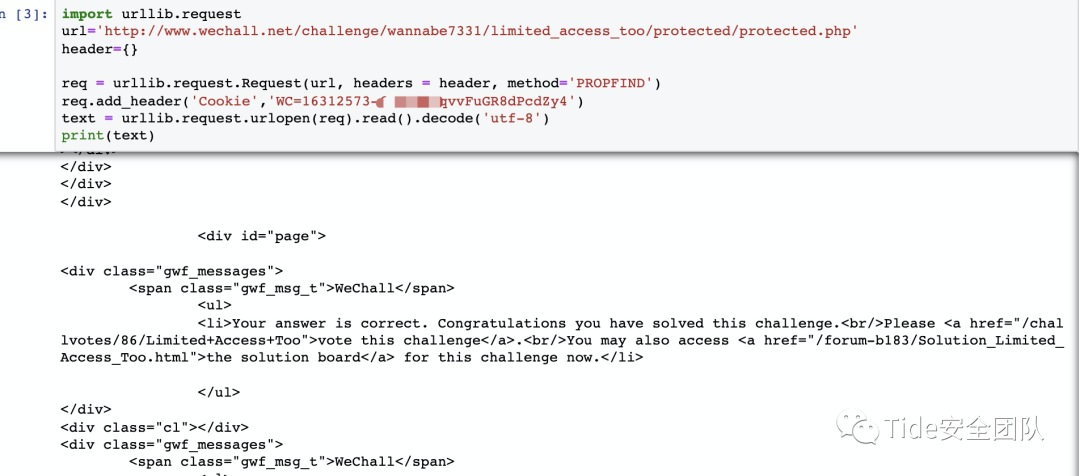
参考大佬的代码:
- import urllib.request
- url='http://www.wechall.net/challenge/wannabe7331/limited_access_too/protected/protected.php'
- header={}
- req = urllib.request.Request(url, headers = header, method='PROPFIND')
- req.add_header('Cookie','WC=Value')
- text = urllib.request.urlopen(req).read().decode('utf-8')
- print(text)
运行后直呼666
0x05 2 Shadowlamb - I by Gizmore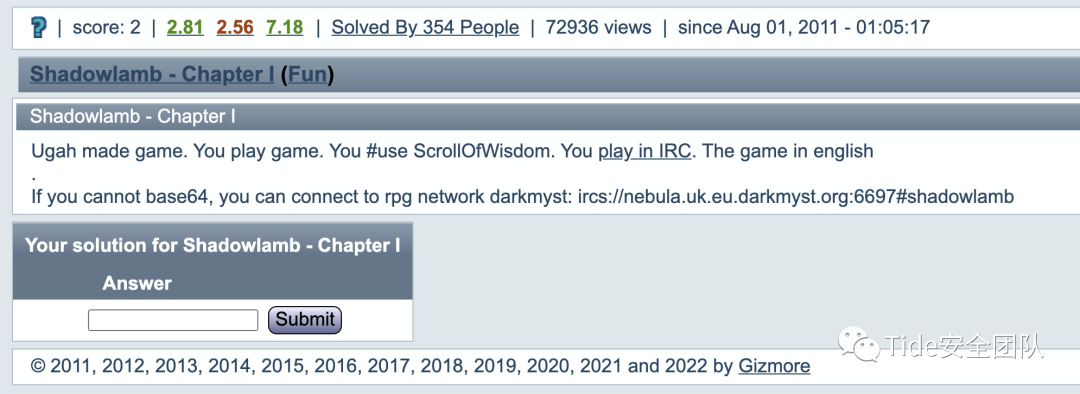 
题目意思:
Ugah 制作的游戏。你玩游戏。你#use ScrollOfWisdom。你在 IRC 玩。英文游戏。
如果不能base64,可以连接rpg网络darkmyst:
ircs://nebula.uk.eu.darkmyst.org:6697#shadowlamb
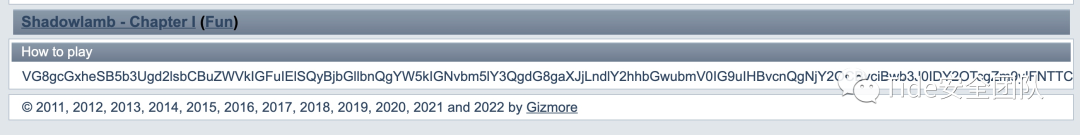 
VG8gcGxheSB5b3Ugd2lsbCBuZWVkIGFuIElSQyBjbGllbnQgYW5kIGNvbm5lY3QgdG8gaXJjLndlY2hhbGwubmV0IG9uIHBvcnQgNjY2OCBvciBwb3J0IDY2OTcgZm9yIFNTTC4KVGhlIGNoYW5uZWwgaXMgI3NoYWRvd2xhbWI=base64解密
解密网站:https://www.qqxiuzi.cn/bianma/base64.htm
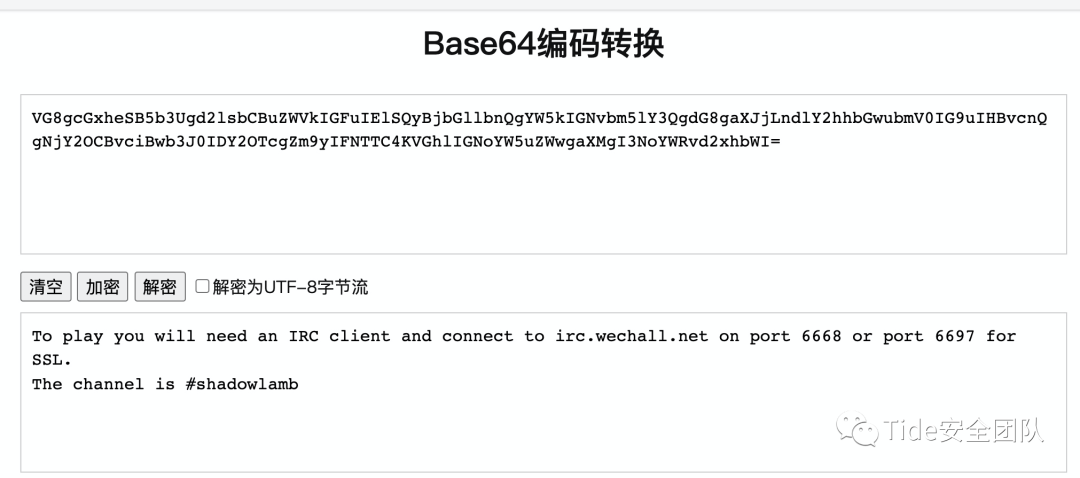 
To play you will need an IRC client and connect to irc.wechall.net on port 6668 or port 6697 for SSL.
The channel is #shadowlamb
IRC
下载xchat地址http://xchat.org/windows/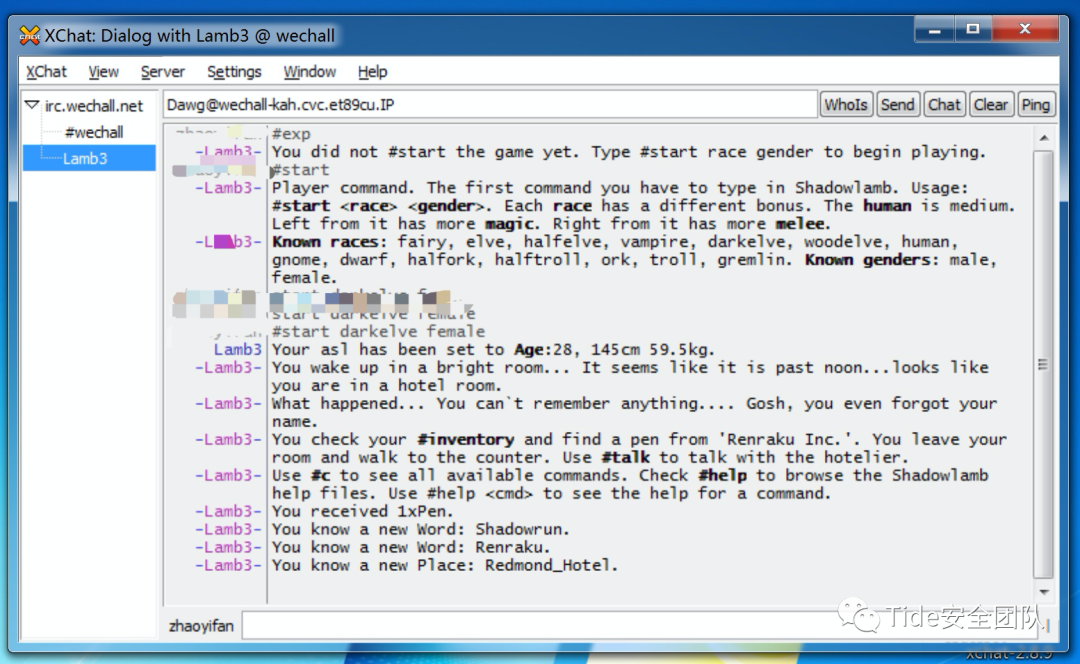 
就。一直玩下去
其实也没玩明白 #attack我编的估计没有用
还有1/3的血,只有110块钱
随地sha人又能随地捡钱的命!
天生没有游戏命
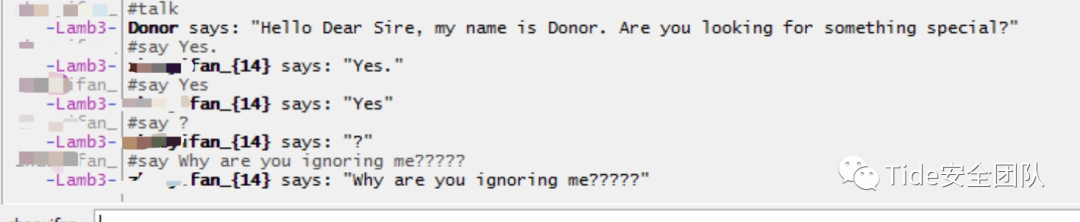 
两个小时过去了,终于抢了800
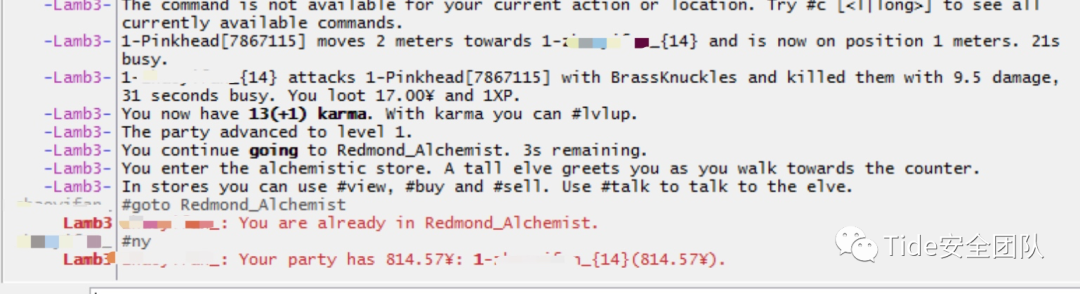 
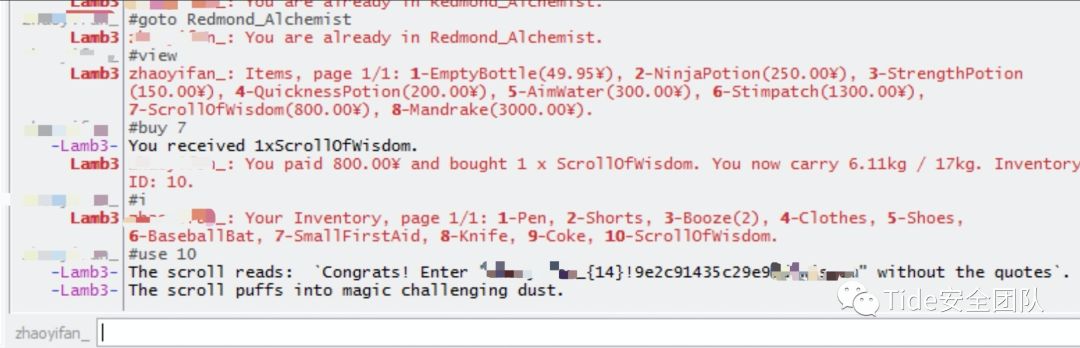
得到flag!这个题没点耐心就跳过去吧
0x06 2 Training: Warchall - The Beginning by WarChallStaff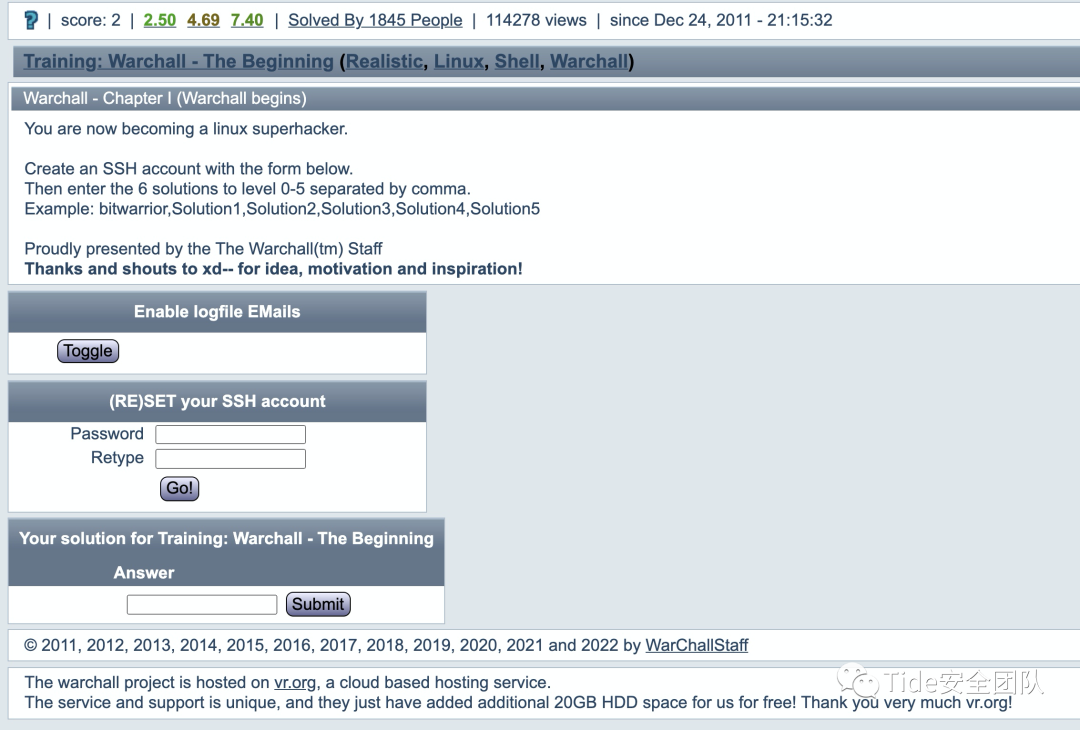 
题目意思:
你现在正在成为一个 Linux 超级黑客。
使用下面的表格创建一个 SSH 帐户。
然后输入 0-5 级的 6 种解决方案,以逗号分隔。
示例:bitwarrior,Solution1,Solution2,Solution3,Solution4,Solution5
设置好密码
 
根据 Exp 推测最终的flag为5个flag拼起来的
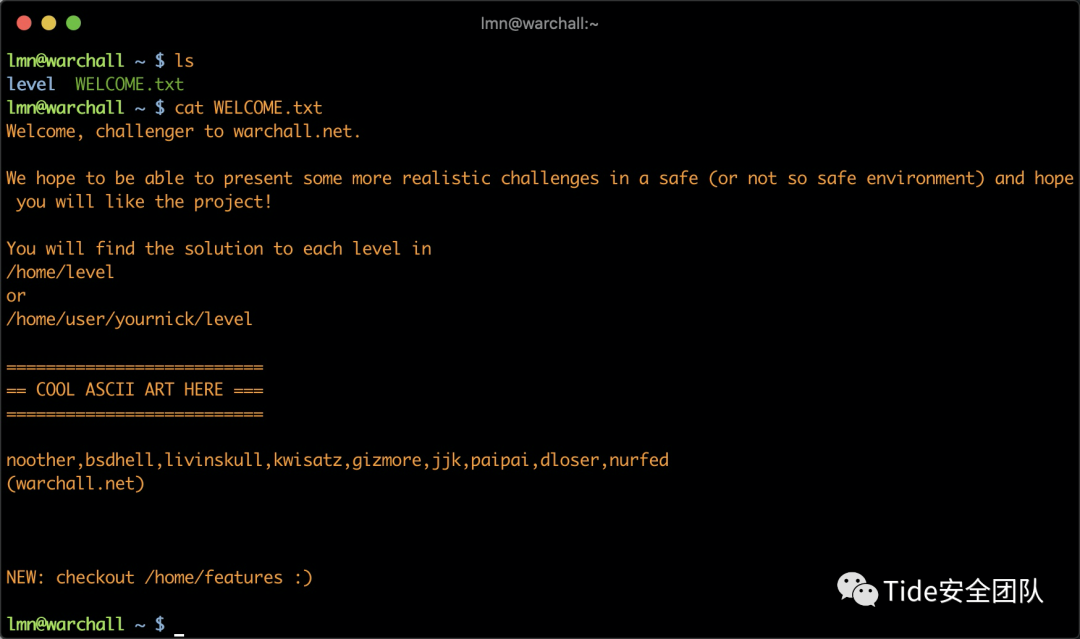 
level 4cat README.txt 发现无权限,授予权限即可
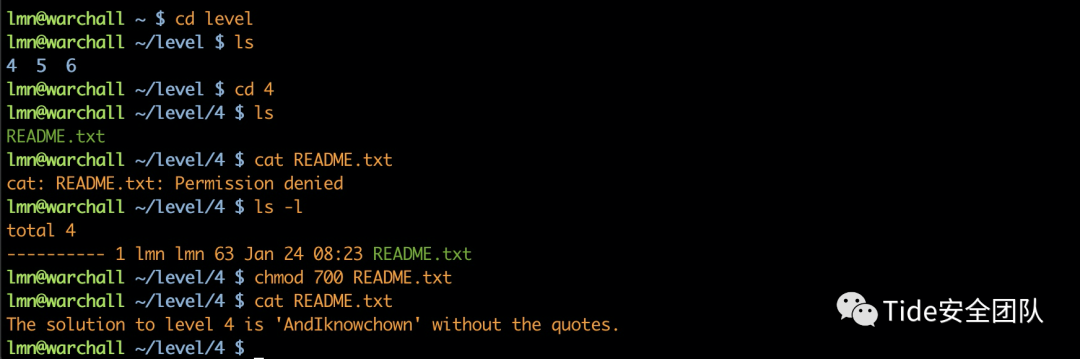 
The solution to level 4 is 'AndIknowchown' without the quotes.
level 5提示:Protect your /home/user/lmn/level directory from other users. Then wait 5 minutes.
解决办法:删除其他用户权限.
 
5文件夹中出现solution.txt,授予权限
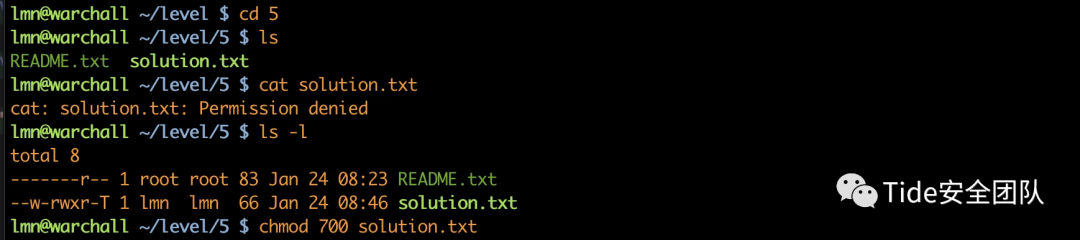 
The solution to level 5 is 'OhRightThePerms', without the quotes.
level 0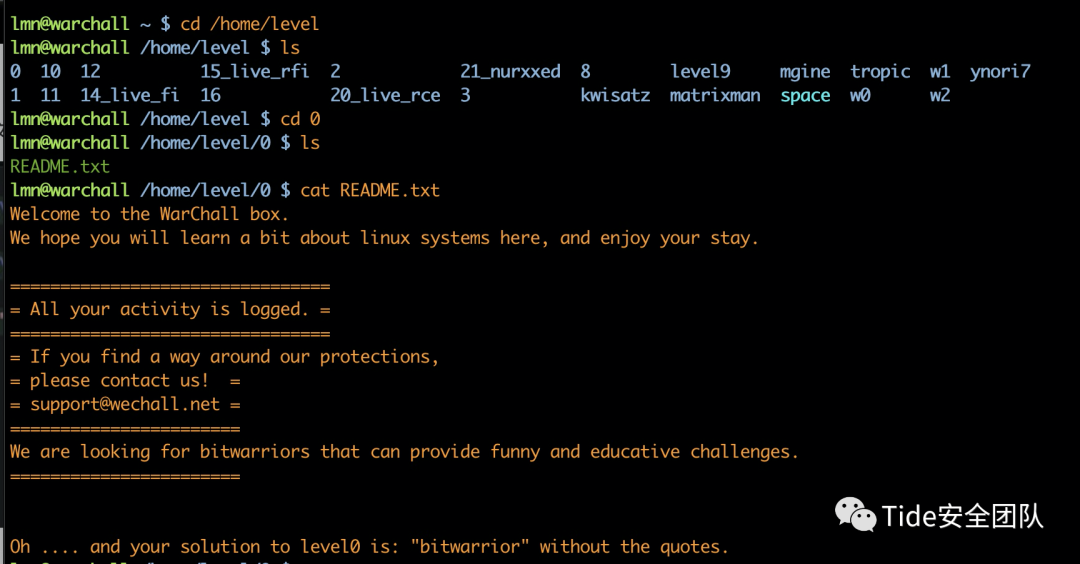 
Oh .... and your solution to level0 is: "bitwarrior" without the quotes.
level 1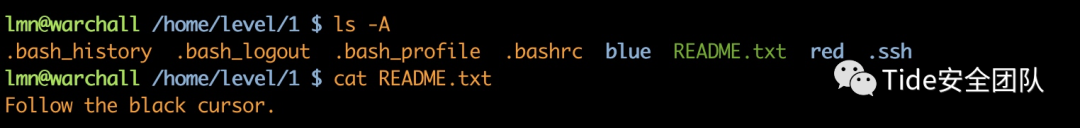 
where??
我是在当前目录做完level 45才开始0123的,发现每个flag都伴随着关键字“solution”那直接搜索一下
方便快捷
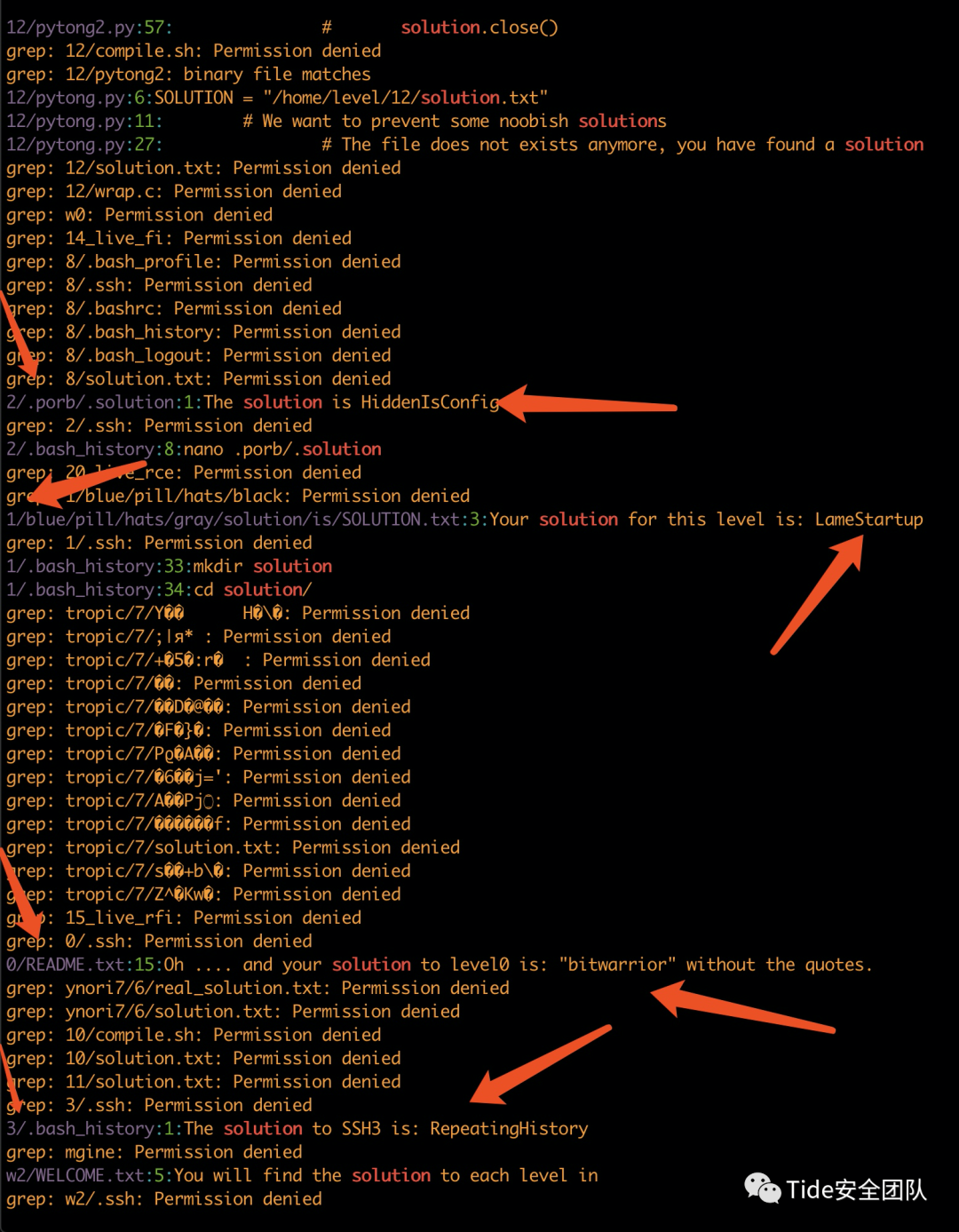 
bitwarrior,LameStartup,HiddenIsConfig,RepeatingHistory,AndIknowchown,OhRightThePerms
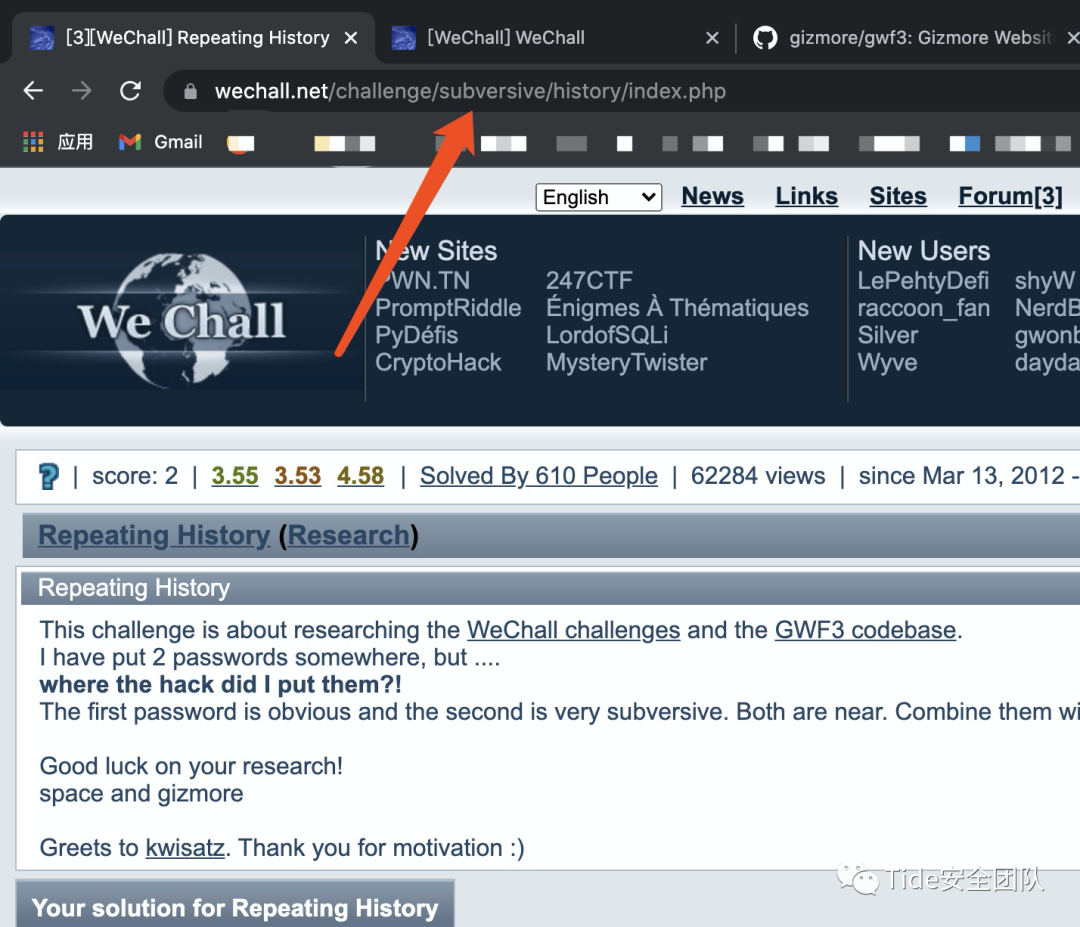
0x07 2 Repeating History by space and Gizmore 
题目意思:
这个挑战是关于研究WeChall 挑战和GWF3 代码库。
我在某个地方放了 2 个密码,但是....
我把它们放在哪里了?!
第一个密码很明显,第二个很颠覆。两个都在附近。将它们组合在一起,无需任何分隔符。
WeChall challenges
GWF3 codebase
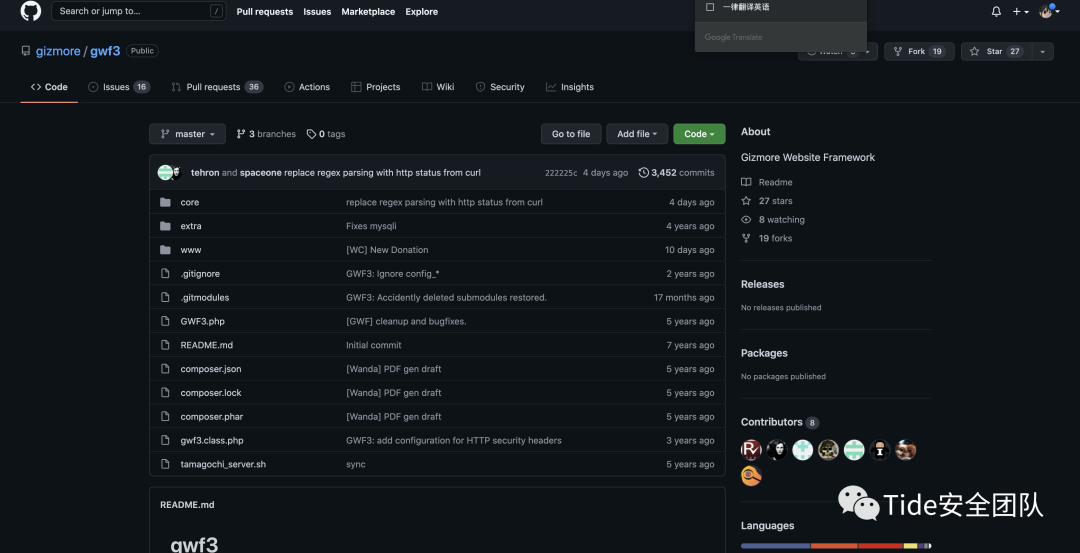 
猜测有一个答案可能放在那些目录下,看到url已经告诉了该题的目录
 
从github查看源码
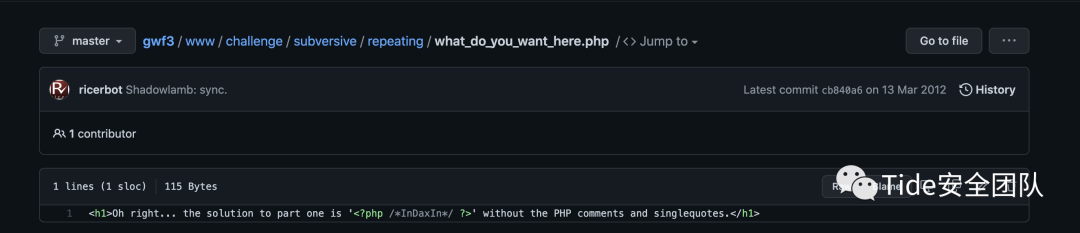 
第一部分:InDaxIn
题目叫Repeating History,那我们就从history里找另一个
搜索关键词:solution
因为第一部分为InDaxIn,是可以读懂的,第二部分也应该是可以读懂的
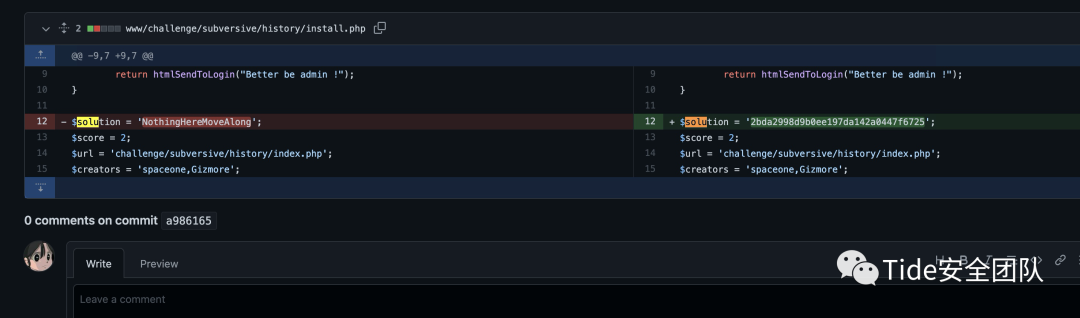 
第二部分:NothingHereMoveAlong
答案:
complete solution:InDaxInNothingHereMoveAlong
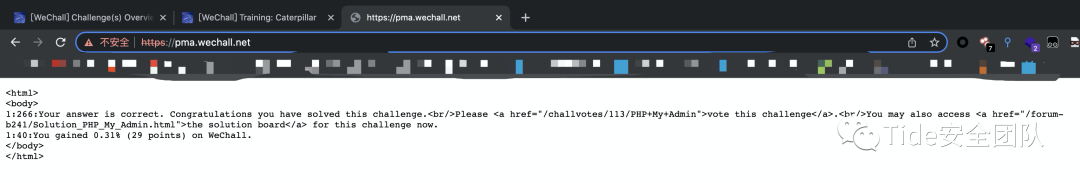
0x08 2 PHP My Admin by Gizmore 
题目意思:
找到隐藏的 PHPMyAdmin 页面,管理员使用该页面来维护微信服务器上的数据库。
就很巧,突然时候发现一句
 
Don't need? I need hint more than anyone else!
根据大佬的思路,在Forums里面看到Evil的留言
Here you got it!
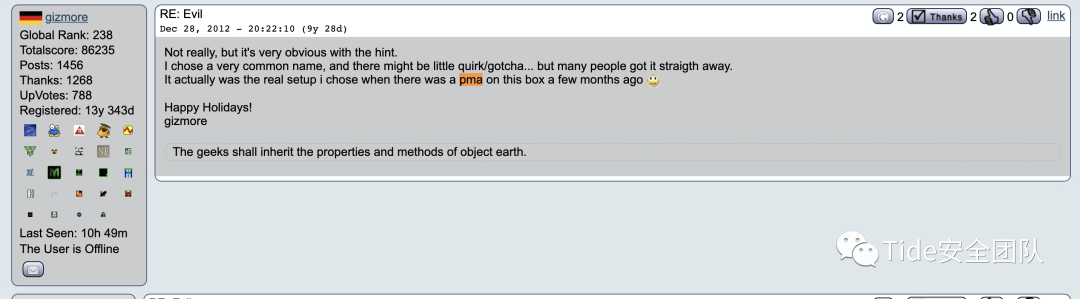 
不在这个子网域????,然后????,you got it
0x09 2 Training: Caterpillar by Gizmore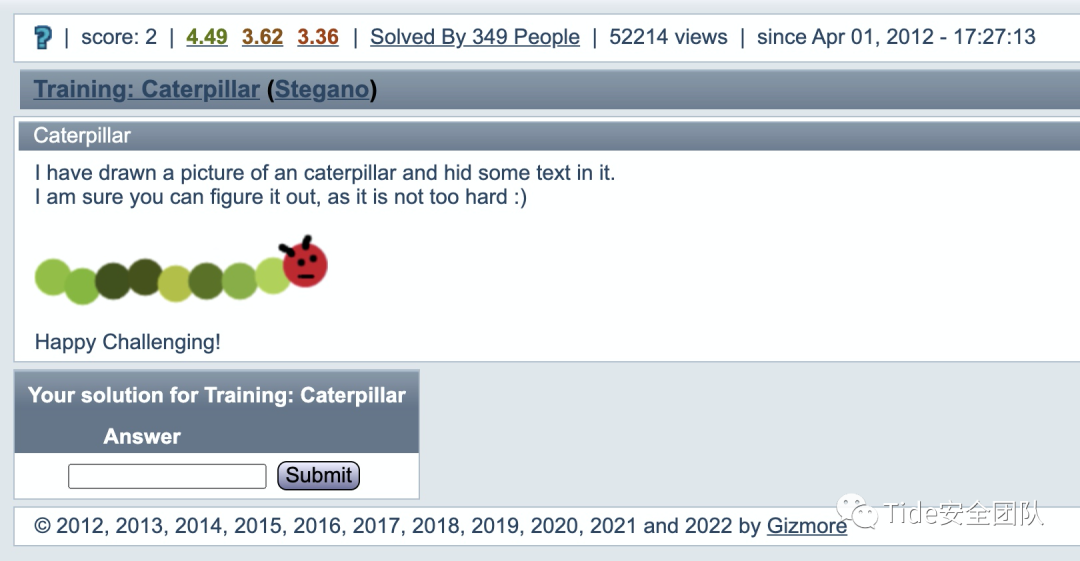 
题目意思:
我画了一张毛毛虫的照片,并在其中隐藏了一些文字。
我相信你能弄明白,因为它不是太难
因为没有思路,借鉴了一下
https://blog.csdn.net/qq_34626094/article/details/113127312的wp
找到图片8个球的HSB值(可惜我没有photoshop,找闺蜜一把梭哈)
 
 
solution: COLOR-SHEMES
0x10 2 AUTH me by Gizmore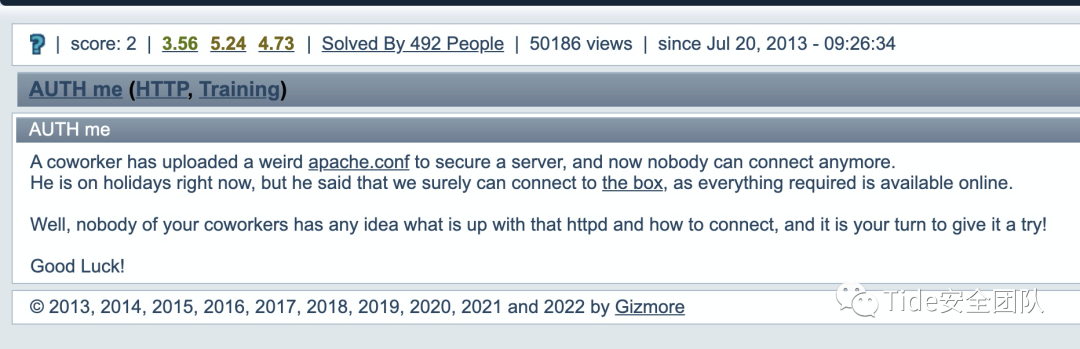 
题目意思:
一位同事上传了一个奇怪的apache.conf来保护服务器,现在没有人可以连接了。
他现在正在度假,但他说我们肯定可以连接到盒子,因为所需的一切都可以在线获得。
好吧,您的同事中没有人知道该 httpd 发生了什么以及如何连接,现在轮到您试一试了!
访问the box
访问不了因为没有证书
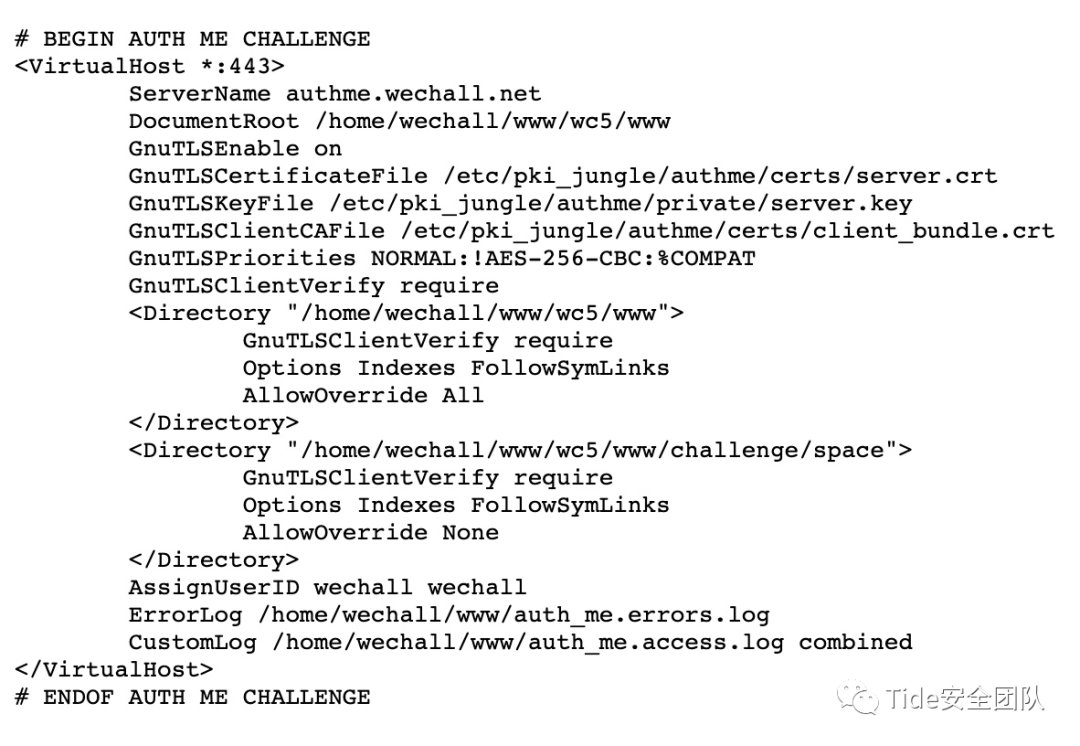 
- ServerName:设置服务器用于辨识自己的主机名和端口号。
- DocumentRoot:设置Web文档根目录。
- GnuTLS是传输层安全的 LGPL 许可实现。
- GnuTLSCertificateFile:整数文件。
我们需要的是客户端证书文件
GnuTLSClientCAFile /etc/pki_jungle/authme/certs/client_bundle.crt题目给了暗示“因为所需的一切都可以在线获得”
在上一级地址获得:
https://www.wechall.net/challenge/space/auth_me/find_me/
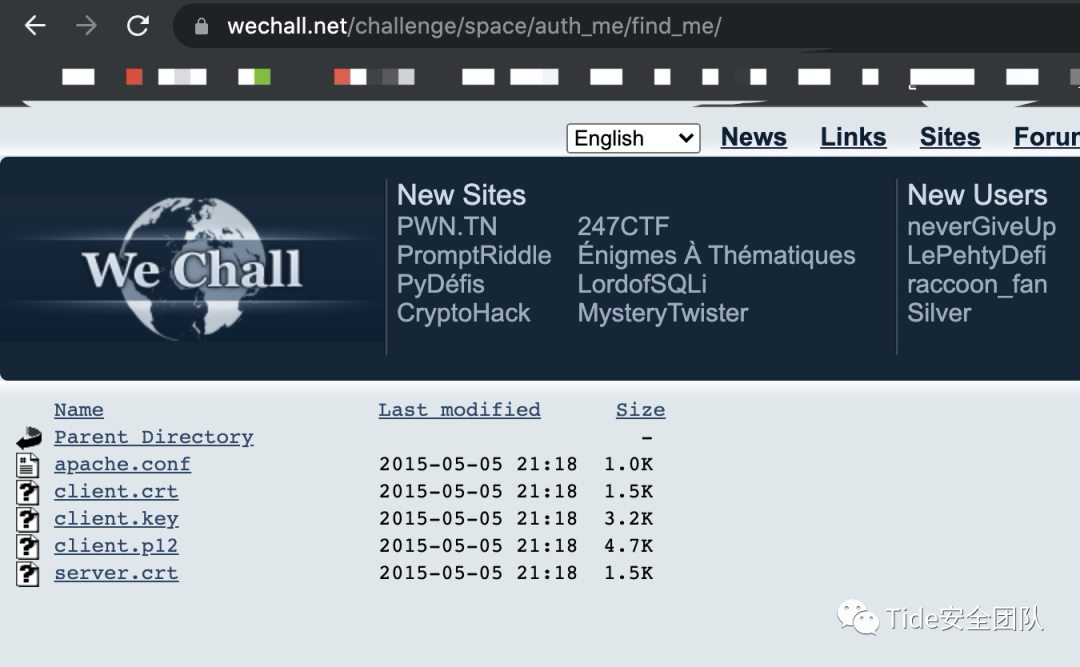 
bingo!
0x11 3 Connect the Dots by galen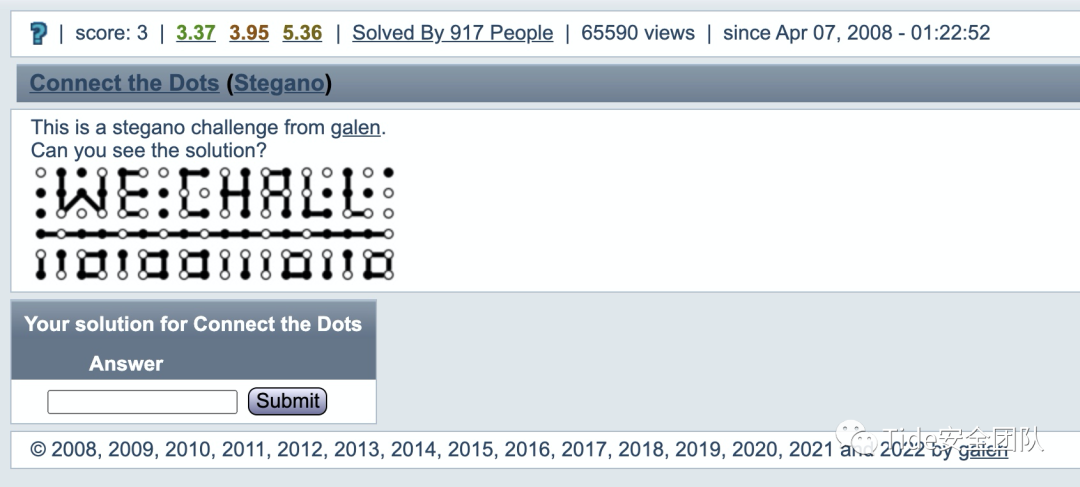 
可以很快看出来像是盲文,找一张盲文表对照一下
 
两行的答案分别是:
T H E S O L U T I
O N I S S K U N K
提交:skunk
0x12 3 hi by Gizmore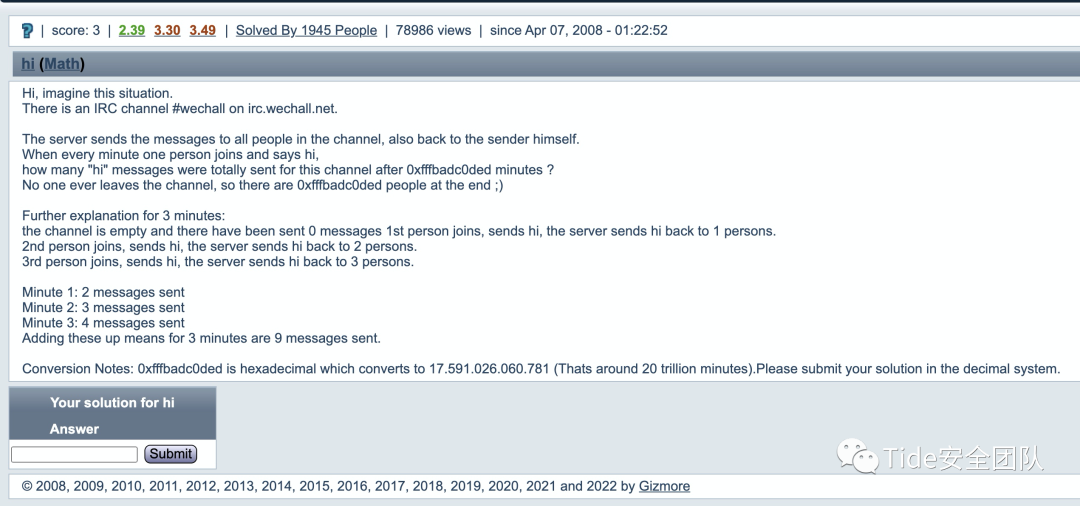 
题目意思:
嗨,想象一下这种情况。
irc.wechall.net 上有一个 IRC 频道#wechall。
服务器将消息发送给频道中的所有人,同时也返回给发送者本人。
当每分钟一个人加入并打招呼时,
在 0xfffbadc0ded 分钟后,该频道总共发送了多少条“hi”消息?
没有人离开频道,所以最后有 0xfffbadc0ded 人;)
3 分钟的进一步解释:
频道是空的,已经发送了 0 条消息 1 人加入,发送 hi,服务器将 hi 发送回 1 人。
第 2 个人加入,发送 hi,服务器将 hi 发送回 2 个人。
第 3 个人加入,发送 hi,服务器将 hi 发送回 3 个人。
第 1 分钟:发送了 2 条消息
第 2 分钟:发送了 3 条消息
第 3 分钟:发送了 4 条消息
将这些相加意味着 3 分钟发送了 9 条消息。
转换说明:0xfffbadc0ded 是十六进制,转换为 17.591.026.060.781(大约 20 万亿分钟)。请以十进制提交您的解决方案。
问题是:在 0xfffbadc0ded 分钟后,该频道总共发送了多少条“hi”消息?
构造一个表达式(有点丑意思对了)
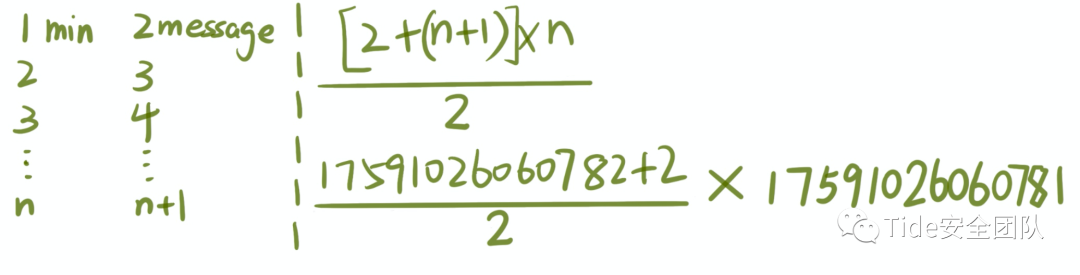 
网站地址:https://www.wolframalpha.com/input/?i=17591026060781*17591026060784%2F2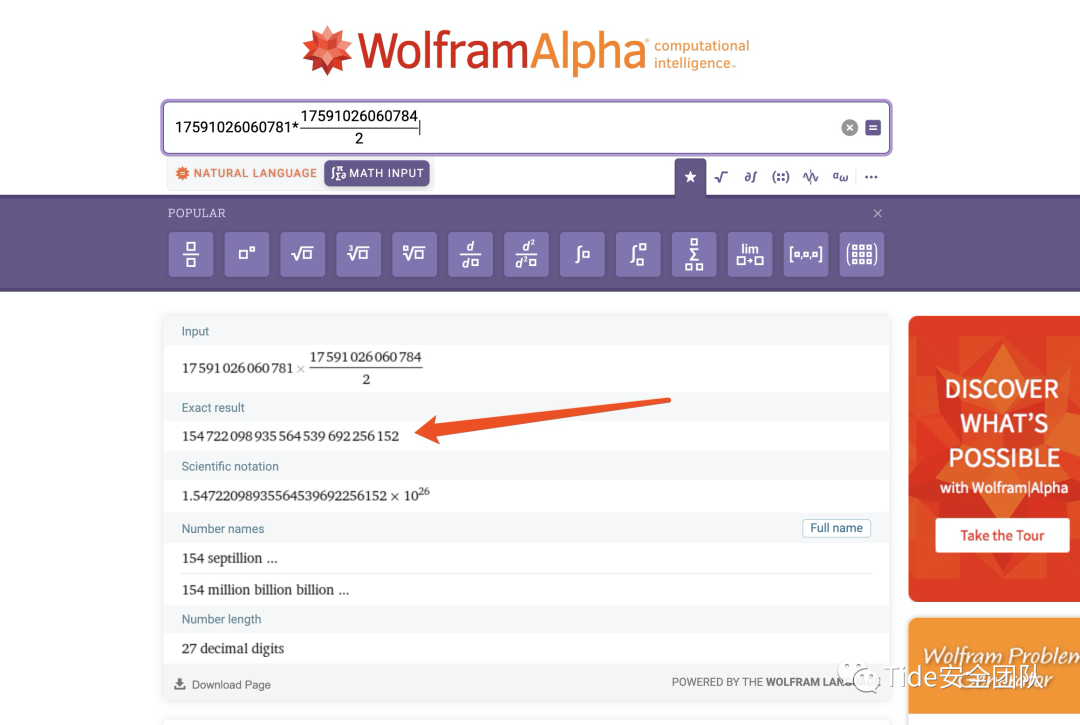 
答案:
154722098935564539692256152
0x13 3 Stegano Woman by Z 
题目意思:
Z 的另一个挑战。
您可以在此处下载。
下载下来的图片:
这道题在图片没有找到什么有用信息,但是在zip里找到这么一段由09 20两种表达的一段字符
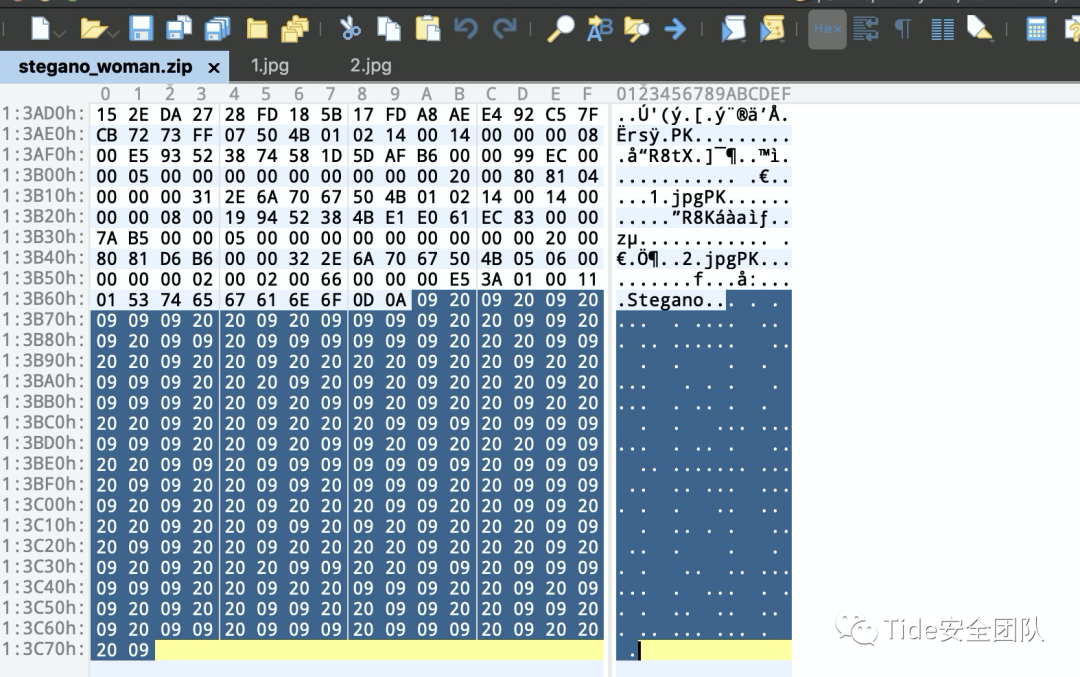 
仔细思考一下两种不同的可以考虑什么编码
09 tab
20 space
尝试一下摩斯密码
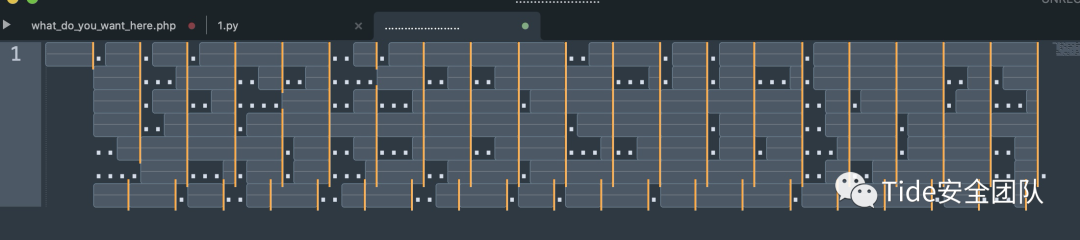 
可是怎么分割呢?
想象一下09是0,20是1
还记得之前有道题提供的工具么
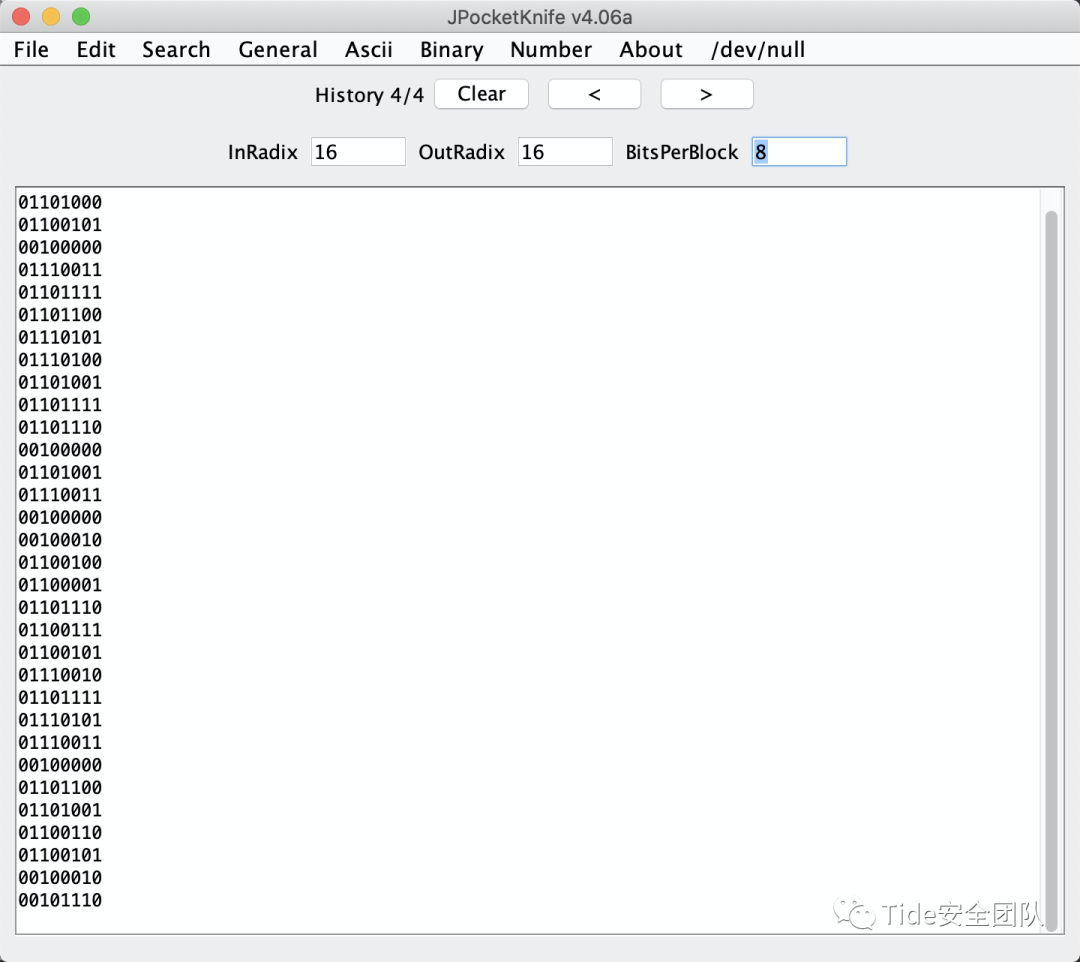 
正好可以format成8位为一组
解出结果
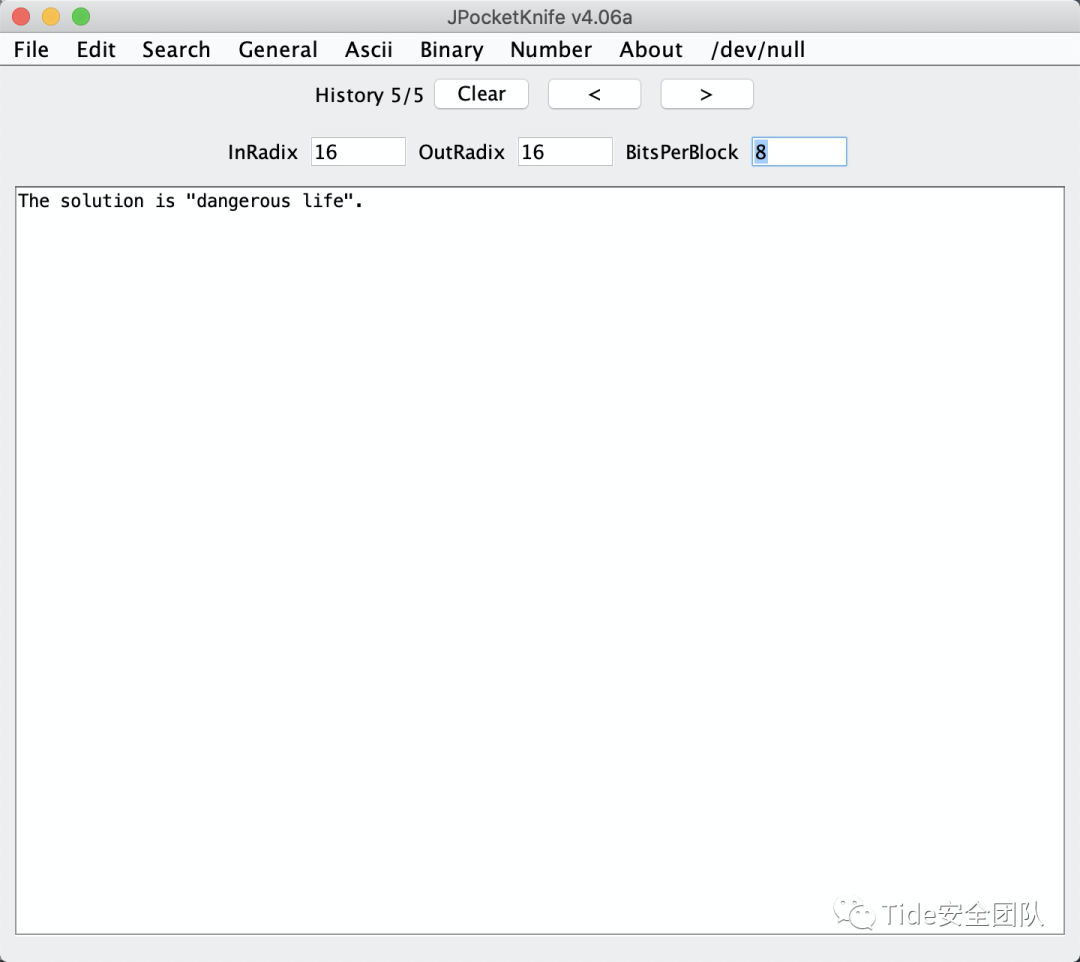 
The solution is "dangerous life".
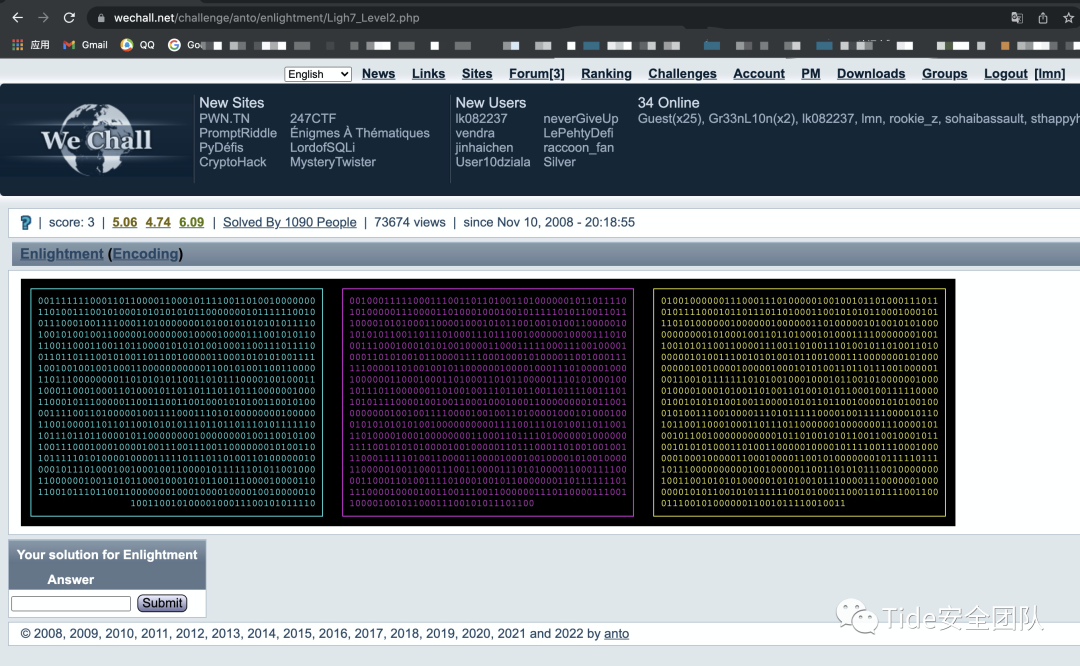
0x14 3 Enlightment by anto 
看到光了么?
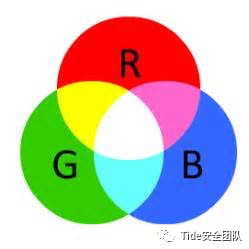 
既然是看到光,那就是三个颜色叠加
代码:
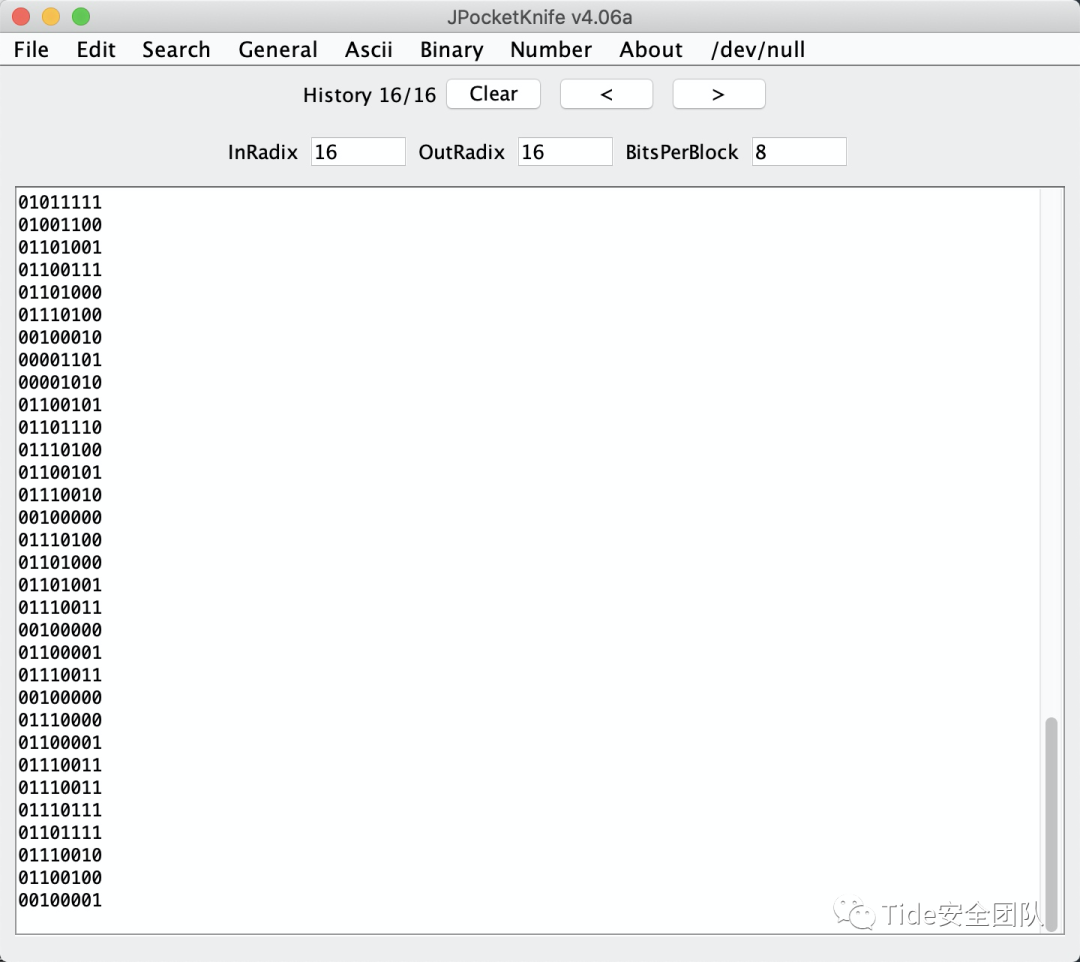
R = '00000000011000000110000000000000000000000100000000010000000000000111000000100100001000000110100100010000000000000010100101100101011001000010000000000000000000000101010000000000011000100010000100101100011000000101000000100000001010010000001000000000000000000000100100000010011101000010000101000000011000010100001000010100011000010100011000100000001000000000010000000010000101110000010101101000001010000010000001100100000000010000000001000010001011100000000001110100000000100010000000010100011000000100000100100000000001100010010001011000011101000010000000100011011101000100000100100111010001000000110000000000010001100010001100100000011101000100100001100001010100000100010100110010000010010000101000000000001000010000000000010000001100010010000100110000001100000001000000010001001000000000000000100001000000000010000000110001000100000000000000000000001000000011000000000001000100000001000100000000000100000011000100000000000000010011000000000000001000000000110100001000000100000001000000100000001000000011000000000001000000000000000100100000000100010010000000010000001000010001000100000001000100000011000000010001001100000000000000010001000000000000000000010000000000000000000100100001000000000011000000110001000000000011000000001000000000000000000000000000000100010011000000100000000100010000000000110000000100000010000100110000000100000010000000110000001100000001000100100000001000000001000000010000001000000000000000000000000100000010000000010000001100000001000100000000001000000001000000010000000010000000100000100000001100000001000000010000000000000000000000010000001100000000000000110001001000010001000100000000000100000000000000000000001100000001000100110001001100000000000100110000000100000011000000000000000100000001000100110000000100000011000000000000000100000000000100000000'G = '01000001011010000010000000000000000000000000000101100100000000000100000000100100010001000000010000100010000000000011100101000110011000000000000000100101010011000010000000000000001100110100100101100000001001010000000001000000001010000010011001100110001000000110100001000100010000000100010100110010001000000010000000110000001010010110000000000101000000010000100000001000010101110010000101000100010011000010000001000000001001100000000001100000000011010000000000010000011011100010000001100000001000000100010000000000011011000100010100010000001100000000000000110000000100000110000101100000011001010000110000000000010001010100010100100000000001000110100000000101011100100110010000000000000011010000000000110000000000000001000000110000000000000011000000010000000000000001000000010000000000010001000000110000000100000001000000000000000100000001000100110000000100000011000000110000001000010010000000010000000100010000000100110000000100010010000000010000001100000000100000000010001000000011000000010001000100000001000000100000001100000001000000010000001100000001000000000000000100000001000100110000001000010011000000100000000100000011000000100000001100000011000000010000000100000011000100010001001100000010000000000001000000000000000000000100000000100011000000100001001100010010000000110000001000010001000100000000000000000000000000100001001000000001000000100000000000000000000100010000000100000010000100100000001000000011000000000000001100000000000000010000001000010011000100110000000000000011000100010000000011000000100000010000000100000000000100010000001100010001000100000001001000000011000000100001001000000011000000000000000100000010000000110000001000000010000100100000000000000001000000100000001100000000000000110000001100010001000100110000001000000001000000110000000000000000100000001000'B = '01000001010000000110000100100001001000000000100001000100001000000101001101100001011000010100000101100011001000000110000001001101000100010000000001100011001000110011010000100000010100110010111001001001011000010110010000101000011010000110110000100001000000000010000000101010000100000010010100010000000001000001001101000100000000000110110001000110000000010000010100001000000000010110010101100100011000000010000000110000010011110010000001000101010010100010000001000100000010110010000000100000000010000010000000000000011001000110000001101000001000000000000001000000001000000110000000000101000001010010100000100000001001110000111000100000001100000000100000000100000100100000010000001010000001000000101000010000000100010010000000000000000100000000000000000000001100000010000000100000000100000010000000100001001100000010000000110001001100000010000000000001000100000010000000010001000000000001000100100000001100010000000000000000001100000001000000100000000100000000100100001000000000000000000000100000000000010001000000110000000100010010000100110000001000000001000000100001001000000011000000110000001000010011000000000000000000000010000000110000000000010011000000100000001100000010000000110000000000000000000000110001001100000001000100000101000010000000000000010001001000010000000100010000001000000010000000110000001100000001000000010000001000000011000000110001001000000011000000000000001000010010000000100000000100010001000100110000000000000001000000100000001000010010000100010000001100000011000000100000000001010000001000100000000000000011000000100000000100010010000000110000000000000011000000010000000100010010000000110000001100000011000000100000001000000000000100010001001100000010000000010000001100000000000000000000000000000010000000000001001000000000000000000000001000000000110000001010'for i in range(len(R)): if int(R) | int(G) | int(B): print(1, end="") else: print(0, end="") 
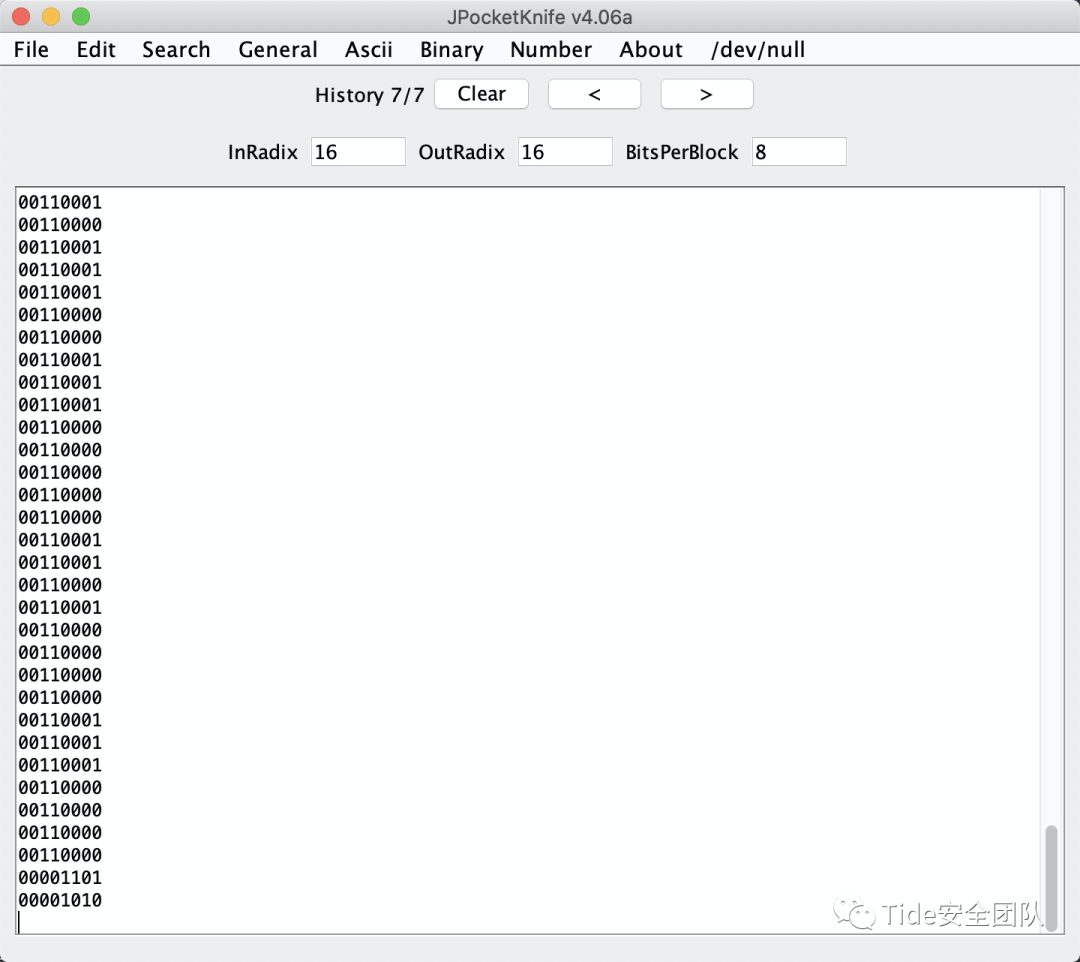
再一次放到那个软件中
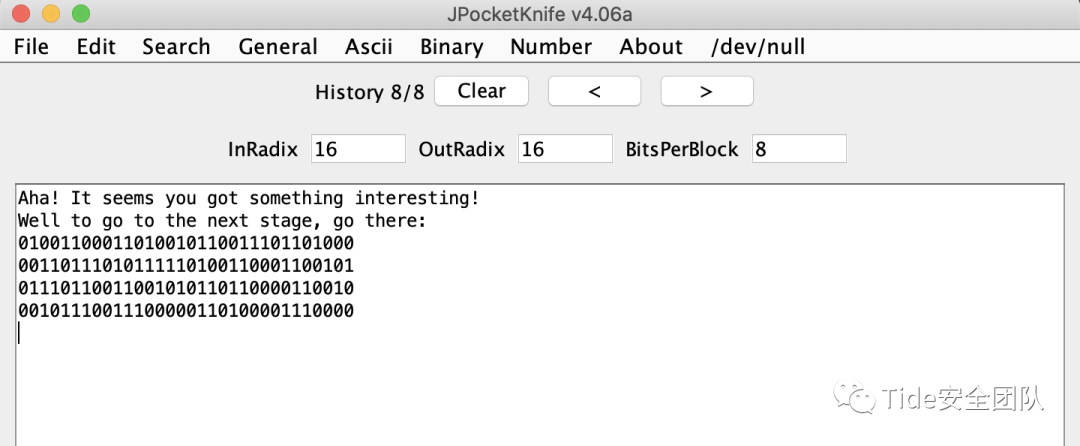 
Aha! It seems you got something interesting!Well to go to the next stage, go there:01001100011010010110011101101000001101110101111101001100011001010111011001100101011011000011001000101110011100000110100001110000again!
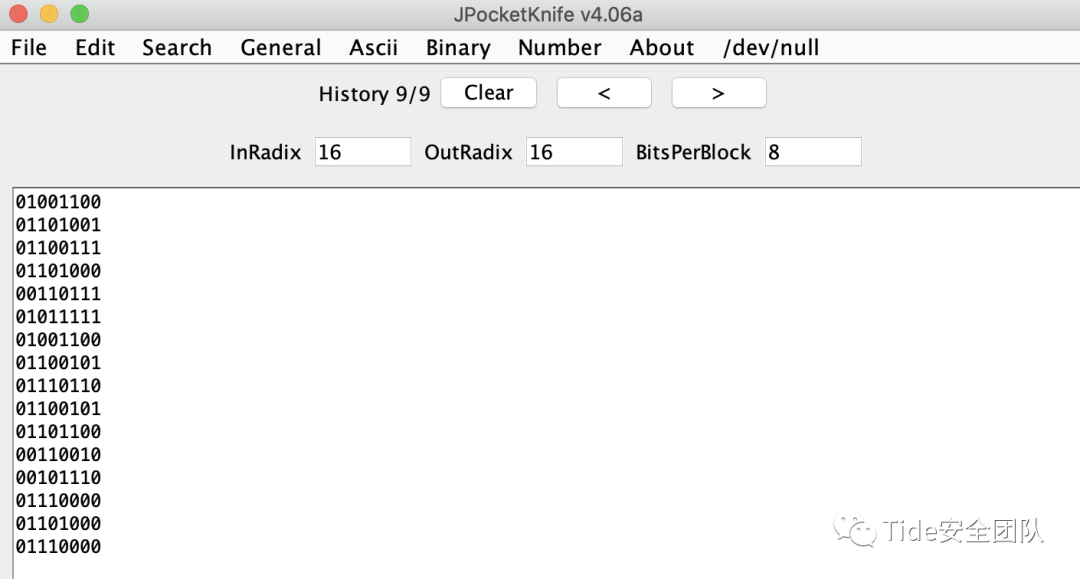 
快看到答案了
这就很有意思了
是这个颜色对吧
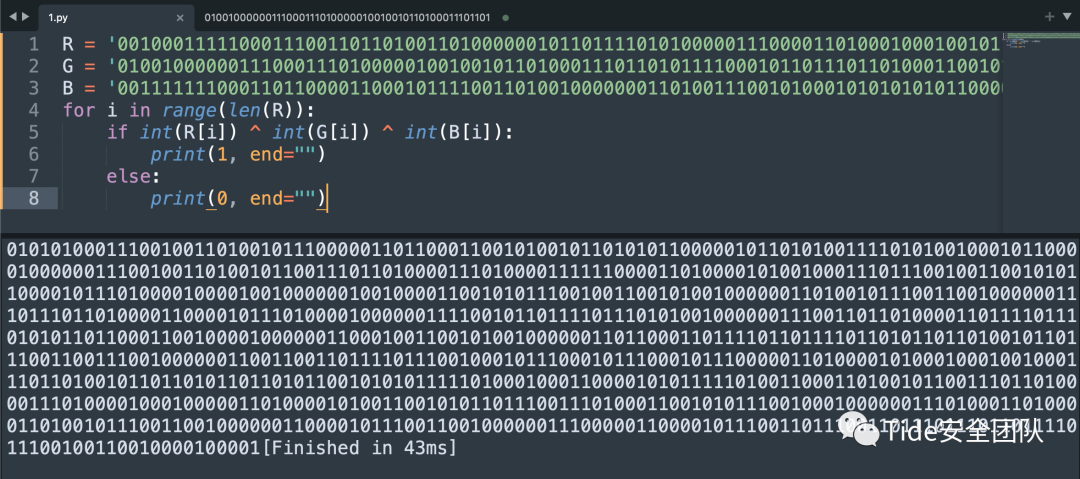 
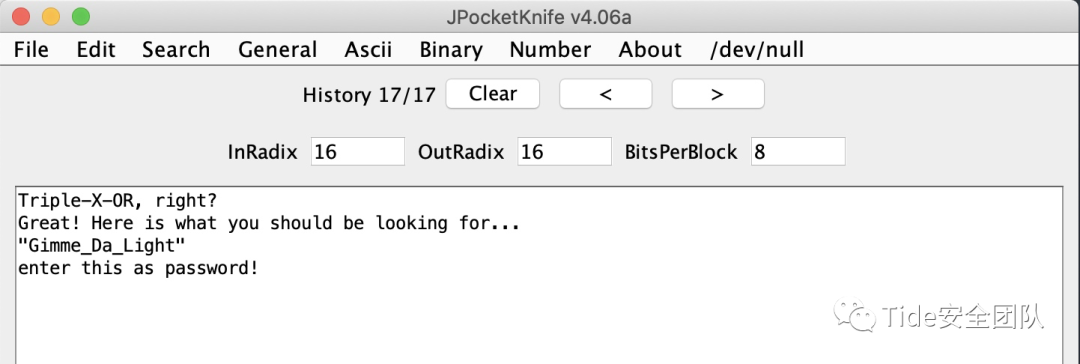 
Triple-X-OR, right?
Great! Here is what you should be looking for...
"Gimme_Da_Light"
enter this as password!
0x15 3 Simply Red by anto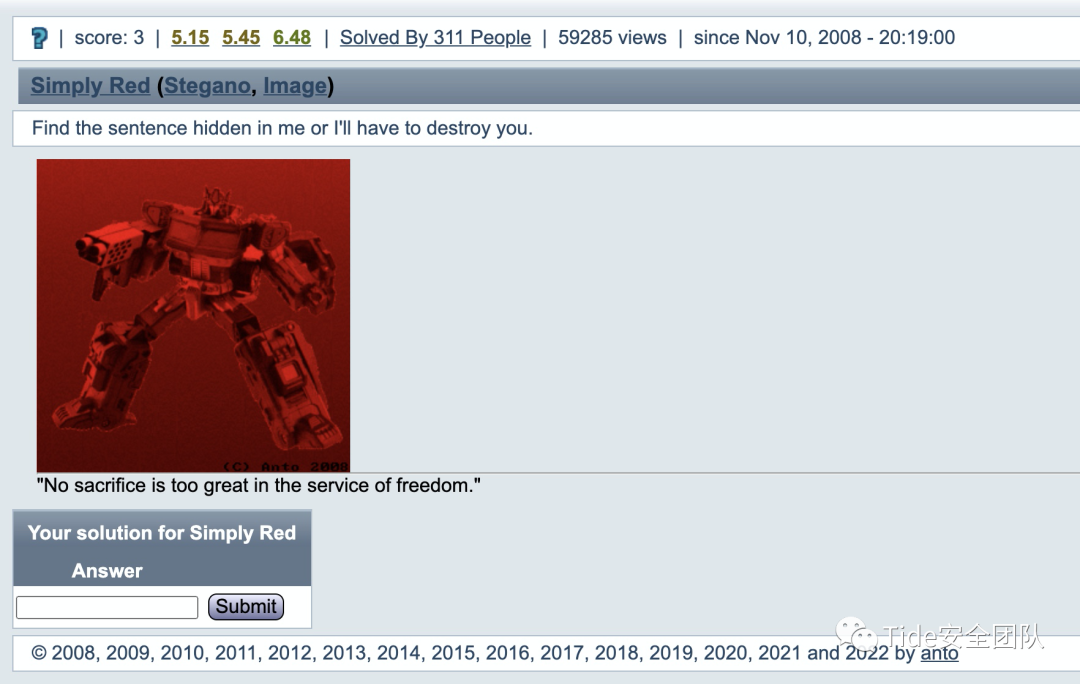 
题目意思:
找出隐藏在我身上的那句话,否则我将不得不摧毁你。
“在为自由服务的过程中,任何牺牲都不算大。”
既然从根本开始做,那就假设我不知道这是谁,既然是饮用那就是他说出的话,搜索一下
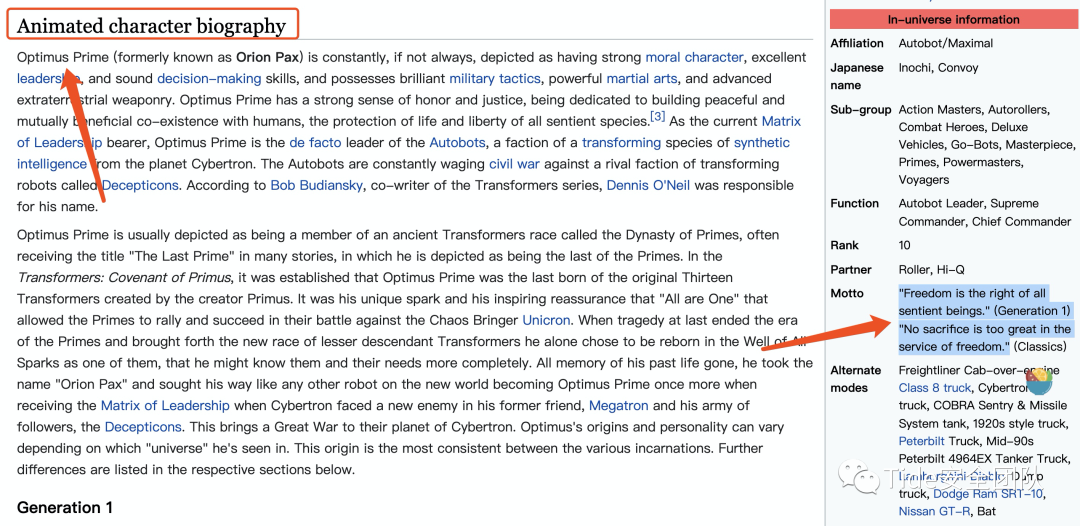 
我们知道原来它叫 Optimus Prime
第一眼竟然认成了 Option Prime
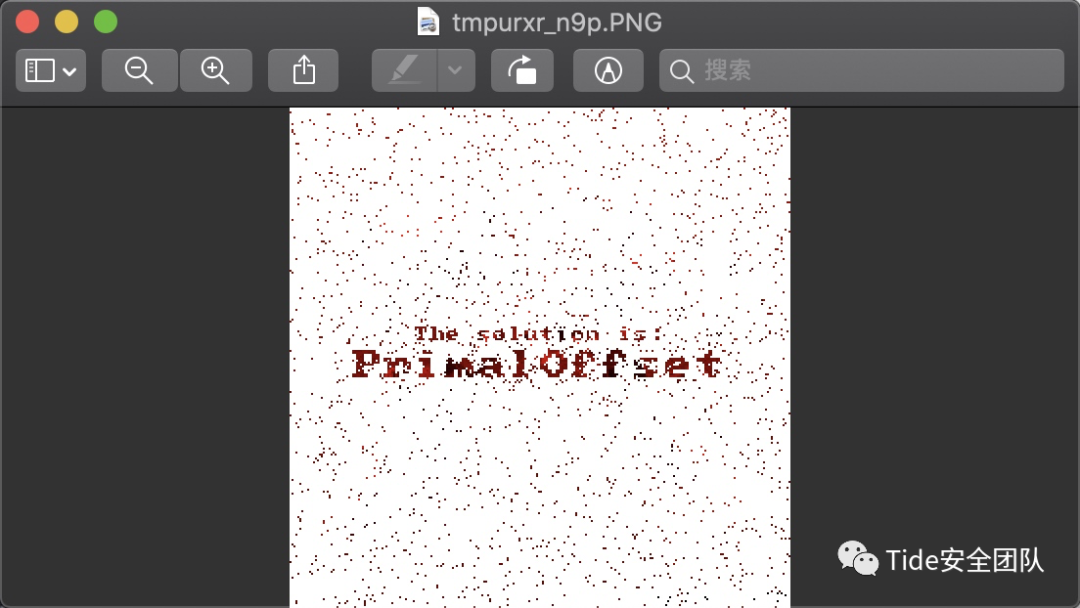
分析一定与素数有关,并且是红色为底色,之前有一道题是提图片的HSB,既然是红色,那就分析像素的R为素数尝试一下
在搜索代码的时候发现已经有大佬写出了这个代码
地址:https://www.tuziang.com/index.php/combat/1985.html
from PIL import Imagefrom math import sqrtdef is_prime(n): if n==1: return False for i in range(2, int(sqrt(n) + 1)): if n % i == 0: return False return Trueimg = Image.open("op.png")width = img.size[0]height = img.size[1]for x in range(width): for y in range(height): r,g,b = img.getpixel((x,y)) if is_prime(r): continue else: img.putpixel((x,y),(255,255,255))img.show() 
参考链接????:http://www.chiange.com/http://ww ... og/2013/07/gpg.html[/url]虽然昨天刚更新今天又更新了,因为昨天是上星期写的,这两篇零零散散的时间写了二十多天,不过这些都不重要,和大家一起进步最重要????
|
|